NODEBB: Nginx error performance & High CPU
-
Hello
Since yesterday, we have been experiencing a massive influx of new users.
Today we have more than 1000 simultaneous connections (account creation, participation in topics, etc.)
I had a lot of issues with Nginx that I think I got fixed.
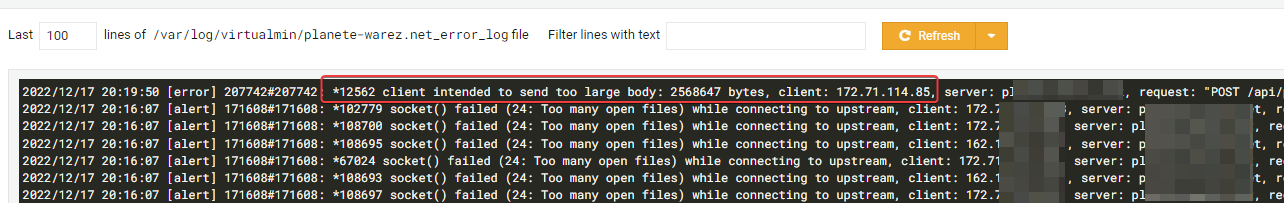
I have several “worker_connections is too long” & “too many openfiles” errors on nginx log :
I think I solved his 2 problems in the following way :
systemctl edit --full nginx.service [Service] LimitNOFILE=70000 nano /etc/nginx/nginx.conf worker_rlimit_nofile 70000; events { # worker_connections 768; worker_connections 65535; # multi_accept on; multi_accept on; } I have “client intended to send too large body” errors too :
I think I solved this problem in the following way :
nano /etc/nginx/nginx.conf http { ## # Basic Settings ## client_max_body_size 10M; –> I hope this will be enough for Nginx.
But now, I have a problem of CPU performance (sometimes, not ) which causes nodebb 503 errors (not nginx) or latencies because nodeJS and mongodb takes a lot of CPU.
– Would there be tweaks for nodejs, nodebb or mongodb to prevent the influx of users from draining the CPU - RAM ?
– If you have better values for nginx error (see above the topic) or better fix, tell me

Thanks in advance @phenomlab
-
Hello
Since yesterday, we have been experiencing a massive influx of new users.
Today we have more than 1000 simultaneous connections (account creation, participation in topics, etc.)
I had a lot of issues with Nginx that I think I got fixed.
I have several “worker_connections is too long” & “too many openfiles” errors on nginx log :
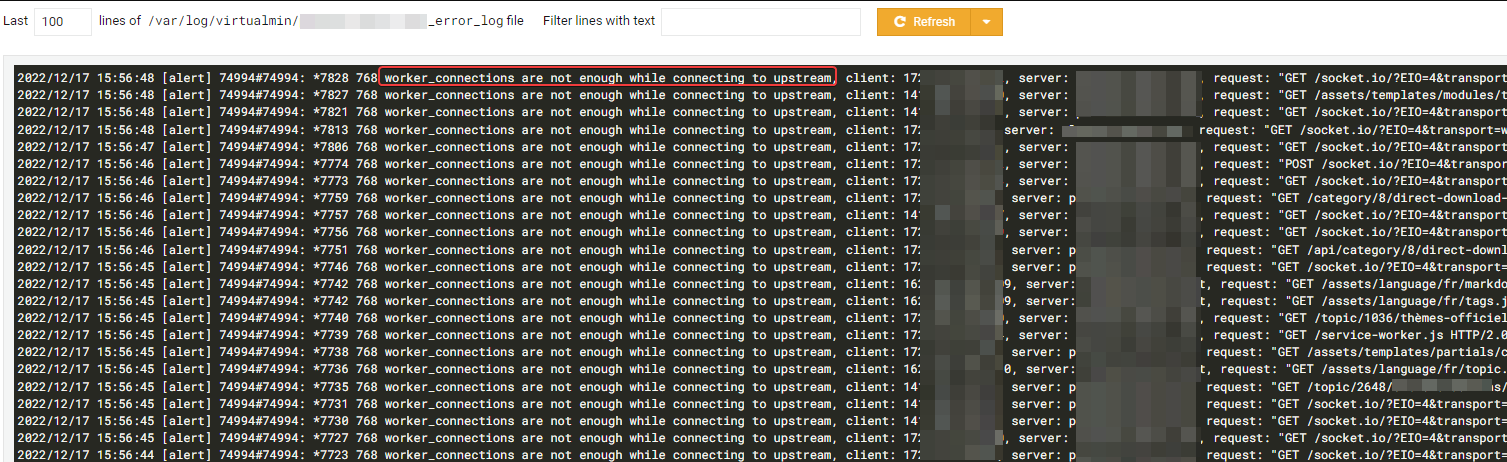
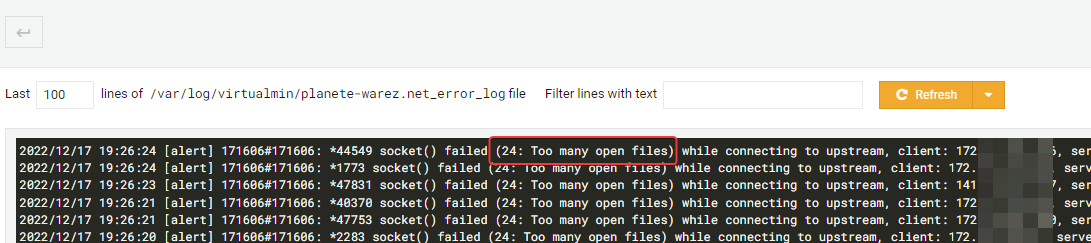
I think I solved his 2 problems in the following way :
systemctl edit --full nginx.service [Service] LimitNOFILE=70000nano /etc/nginx/nginx.conf worker_rlimit_nofile 70000; events { # worker_connections 768; worker_connections 65535; # multi_accept on; multi_accept on; }I have “client intended to send too large body” errors too :

I think I solved this problem in the following way :
nano /etc/nginx/nginx.conf http { ## # Basic Settings ## client_max_body_size 10M;–> I hope this will be enough for Nginx.
But now, I have a problem of CPU performance (sometimes, not ) which causes nodebb 503 errors (not nginx) or latencies because nodeJS and mongodb takes a lot of CPU.
– Would there be tweaks for nodejs, nodebb or mongodb to prevent the influx of users from draining the CPU - RAM ?
– If you have better values for nginx error (see above the topic) or better fix, tell me

Thanks in advance @phenomlab
@DownPW my immediate concern here is that your server may well be the victim of a DDoS attack. Suddenly seeing this many new connections isn’t typical of organic traffic, and my suggestion would be to immediately reverse any changes you made to the nginx config to accommodate this additional load.
NodeBB by default has rate limiting capabilities (hence the 503 message you’re experiencing). I would personally start with checking the source IP addresses to see where they originate from, and how quickly they are establishing sessions. If you find that you are connections from multiple ip address within secondd of each other, then this is not organic traffic.
I know the domain itself is via Cloudflare but the server IP may be exposed somewhere meaning it is vulnerable to direct attack
Do you see any raised activity within fail2ban for example?
-
@DownPW my immediate concern here is that your server may well be the victim of a DDoS attack. Suddenly seeing this many new connections isn’t typical of organic traffic, and my suggestion would be to immediately reverse any changes you made to the nginx config to accommodate this additional load.
NodeBB by default has rate limiting capabilities (hence the 503 message you’re experiencing). I would personally start with checking the source IP addresses to see where they originate from, and how quickly they are establishing sessions. If you find that you are connections from multiple ip address within secondd of each other, then this is not organic traffic.
I know the domain itself is via Cloudflare but the server IP may be exposed somewhere meaning it is vulnerable to direct attack
Do you see any raised activity within fail2ban for example?
I don’t think it’s DDOS attack.
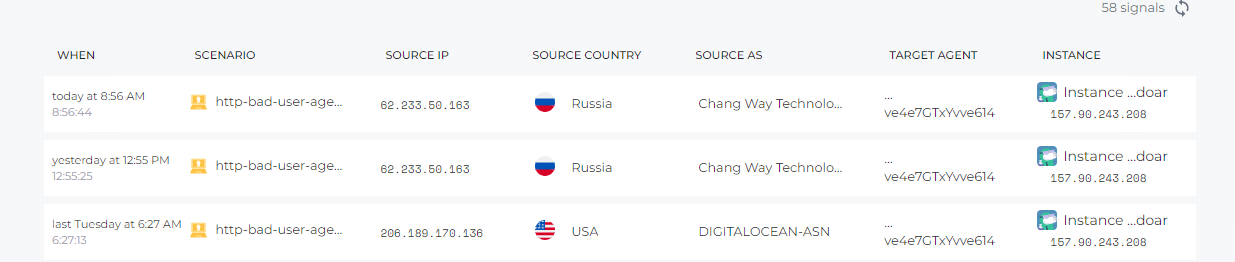
Indeed, I am already equipped with anti DDOS musers with crowdsec software. This one did not detect DDOS on the serverOn 2 days ago, we have just two HTTP bad user agent scan on the server but not ddos attack
In fact, for the record, a very reputable illegal site closed with a text file pointing to one of our topics that talked about it. This caused a massive influx of users. We could see it in the number of connections as well as in the numbers of people coming to register permanently.
I don’t really want to undo all the nginx modifications because it’s thanks to this one that the server is stabilized
After if you have tweak against the ddos attack, I really want to know them and apply them
but for me it’s really not that.I’m taking all possible concrete steps but I think the focus should be on optimizing nodeBB too
Actually, we have 758 members online

You can go the server if you want
-
I don’t think it’s DDOS attack.
Indeed, I am already equipped with anti DDOS musers with crowdsec software. This one did not detect DDOS on the serverOn 2 days ago, we have just two HTTP bad user agent scan on the server but not ddos attack
In fact, for the record, a very reputable illegal site closed with a text file pointing to one of our topics that talked about it. This caused a massive influx of users. We could see it in the number of connections as well as in the numbers of people coming to register permanently.
I don’t really want to undo all the nginx modifications because it’s thanks to this one that the server is stabilized
After if you have tweak against the ddos attack, I really want to know them and apply them
but for me it’s really not that.I’m taking all possible concrete steps but I think the focus should be on optimizing nodeBB too
Actually, we have 758 members online


You can go the server if you want
@DownPW said in NODEBB: Nginx error performance & High CPU:
very reputable illegal site
That statement alone is enough to cause concern in my view. How can it be reputable if it’s an illegal site

I’m still going to reserve judgement on this until I’ve fully reviewed the logs. Nginx was designed to automatically scale to hundreds and thousands of users per second and that is it’s main advantage over Apache. The client body size should not have to be adjusted unless an upload is being performed on the site which would have me concerned as this could be an attempt to deposit a malicious payload.
If you’re confident that this isn’t a DDoS attack, then ok, but you may have just opened the floodgates in terms of removing built in restrictions with nginx. Given the very nature of that site, I’d be exercising caution and would probably recommend enabling the “I’m under attack” . If this is organic traffic and legitimate in intent, then they’ll complete the captcha. If they don’t, then they are bots.
Have you checked random IP addresses in the nginx logs to see if they are listed in the IP abuse database? And if you enable the “I’m under attack” setting I wouldn’t mind bettibg that the number of active users will start to freefall.
Finally, how many new users do you have registered on the site? Presently, I wouldn’t be comfortable with this scenario without a full analysis and review, but I can only recommend here.
-
I don’t think it’s DDOS attack.
Indeed, I am already equipped with anti DDOS musers with crowdsec software. This one did not detect DDOS on the serverOn 2 days ago, we have just two HTTP bad user agent scan on the server but not ddos attack

In fact, for the record, a very reputable illegal site closed with a text file pointing to one of our topics that talked about it. This caused a massive influx of users. We could see it in the number of connections as well as in the numbers of people coming to register permanently.
I don’t really want to undo all the nginx modifications because it’s thanks to this one that the server is stabilized
After if you have tweak against the ddos attack, I really want to know them and apply them
but for me it’s really not that.I’m taking all possible concrete steps but I think the focus should be on optimizing nodeBB too
Actually, we have 758 members online


You can go the server if you want
@DownPW I’ve just started reviewing your
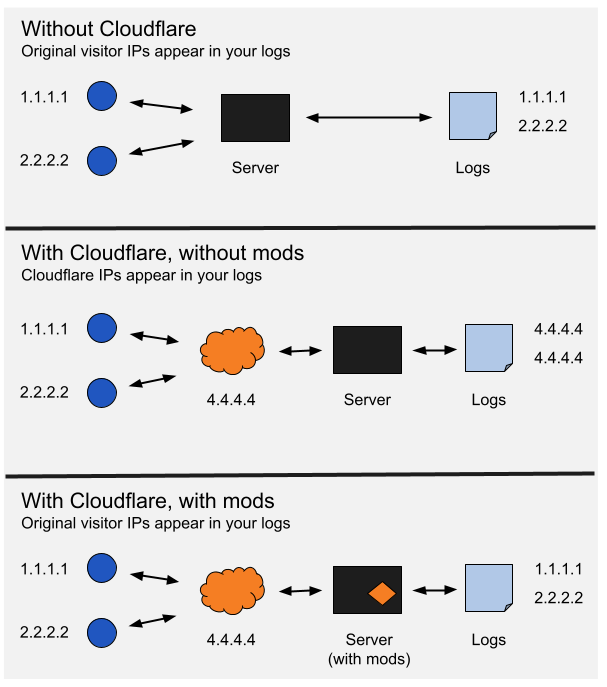
nginx.logand a couple of things immediately stand out for me- Literally all of the IP addresses are within Cloudflare’s subnet ranges. This means that you cannot possibly tell if the traffic is legitimate or not as you do not know what the originating IP addresses are
- The TCP established times are all within seconds of each other but from different IP addresses. This very much lends itself towards the traffic not being organic in my view, but you will never really know the true identity of these connections without first attempting to unpack the TCP headers - see the below
You could temporarily disable Cloudflare on your site to get a quick analysis, then keep an eye on your own DDoS implementation to determine if this traffic is legitimate or not.
The bottom line is this. Don’t be lulled into a false sense of security just because Cloudflare passes the traffic to your site.
-
@DownPW I’ve just started reviewing your
nginx.logand a couple of things immediately stand out for me- Literally all of the IP addresses are within Cloudflare’s subnet ranges. This means that you cannot possibly tell if the traffic is legitimate or not as you do not know what the originating IP addresses are
- The TCP established times are all within seconds of each other but from different IP addresses. This very much lends itself towards the traffic not being organic in my view, but you will never really know the true identity of these connections without first attempting to unpack the TCP headers - see the below
https://support.cloudflare.com/hc/en-us/articles/200170786-Restoring-original-visitor-IPs
You could temporarily disable Cloudflare on your site to get a quick analysis, then keep an eye on your own DDoS implementation to determine if this traffic is legitimate or not.
The bottom line is this. Don’t be lulled into a false sense of security just because Cloudflare passes the traffic to your site.
I don’t understand all you say.
Finally what we can do ?Actually we have 1.1k users online
We have a lot of inscriptions
-
I don’t understand all you say.
Finally what we can do ?Actually we have 1.1k users online
We have a lot of inscriptions
@phenomlab 362 user inscription in two days and many user on just read forum
-
I don’t understand all you say.
Finally what we can do ?Actually we have 1.1k users online
We have a lot of inscriptions
@DownPW said in NODEBB: Nginx error performance & High CPU:
I don’t understand all you say.
Finally what we can do ?My point here is that the traffic, whilst legitimate in the sense that it’s from another site that has closed, could still be nefarious in nature so you should keep your guard up. However, a number of signups can’t be wrong - particularly if they are actually posting content and not performing requests that actually do not pertain to available URL’s on your site.
I see no indication of that, so the comfort level in the sense that it’s legitimate traffic does increase somewhat accompanied by the seemingly legitimate registrations. However, because all the source IP addresses and within the Cloudflare ranges, you have no ability to tell really who they are without performing the steps I outlined in the previous post.
The good news is that your site just got a huge increase in popularity, but with that will always be a need to keep a close eye on activity. It would only take one nefarious actor to potentially bring down your site.
The nginx configuration you’ve applied will indeed alleviate the stress placed on the server but is a double edged sword in the sense that it does make the goalpost much wider in terms of any potential attack.
My advice herein would be to not scale these settings too high. Use sane judgement.
For the NodeBB side, I know they have baked rate limiting into the product but I’m sure you can actually change that behaviour.
Have a look at
/admin/settings/advanced#traffic-managementYou’ll probably need to play with the values here to get a decent balance, but this is where I’d start.
-
@DownPW said in NODEBB: Nginx error performance & High CPU:
I don’t understand all you say.
Finally what we can do ?My point here is that the traffic, whilst legitimate in the sense that it’s from another site that has closed, could still be nefarious in nature so you should keep your guard up. However, a number of signups can’t be wrong - particularly if they are actually posting content and not performing requests that actually do not pertain to available URL’s on your site.
I see no indication of that, so the comfort level in the sense that it’s legitimate traffic does increase somewhat accompanied by the seemingly legitimate registrations. However, because all the source IP addresses and within the Cloudflare ranges, you have no ability to tell really who they are without performing the steps I outlined in the previous post.
The good news is that your site just got a huge increase in popularity, but with that will always be a need to keep a close eye on activity. It would only take one nefarious actor to potentially bring down your site.
The nginx configuration you’ve applied will indeed alleviate the stress placed on the server but is a double edged sword in the sense that it does make the goalpost much wider in terms of any potential attack.
My advice herein would be to not scale these settings too high. Use sane judgement.
For the NodeBB side, I know they have baked rate limiting into the product but I’m sure you can actually change that behaviour.
Have a look at
/admin/settings/advanced#traffic-managementYou’ll probably need to play with the values here to get a decent balance, but this is where I’d start.
I think you’re right Mark and that’s why I come here looking for your valuable advice and expertise

Basically, the illegal site that closed was a movie download site A topic was opened on our forum to talk about it and many came looking for answers on why and how.
You’re actually right about the fact that we can’t be sure of anything and there are bot attacks or ddos in the lot of connexions
I activated the under attack mode on Cloudflare as you advised me to see (just now.) and we will see like you said
As you advised, I also reset the default nginx configuration values and removed my nginx modifications specified above.
I would like to take advantage of your expertise, see a hand from you to properly configure nginx for ddos and high traffic. (What precise modifications to specify as well as the precise values.)
-
I think you’re right Mark and that’s why I come here looking for your valuable advice and expertise

Basically, the illegal site that closed was a movie download site A topic was opened on our forum to talk about it and many came looking for answers on why and how.
You’re actually right about the fact that we can’t be sure of anything and there are bot attacks or ddos in the lot of connexions
I activated the under attack mode on Cloudflare as you advised me to see (just now.) and we will see like you said
As you advised, I also reset the default nginx configuration values and removed my nginx modifications specified above.
I would like to take advantage of your expertise, see a hand from you to properly configure nginx for ddos and high traffic. (What precise modifications to specify as well as the precise values.)
@DownPW ok, good. Let’s see what the challenge does to the site traffic. Those whom are legitimate users won’t mind having to perform a one time additional authentication step, but bots of course will simply stumble at this hurdle.
-
@DownPW ok, good. Let’s see what the challenge does to the site traffic. Those whom are legitimate users won’t mind having to perform a one time additional authentication step, but bots of course will simply stumble at this hurdle.
number of user is better (408) but a lot of loose connexion. navigation is hard
-
number of user is better (408) but a lot of loose connexion. navigation is hard
I have chaneg nginx conf with :
worker_rlimit_nofile 70000;
events {
worker_connections 65535;
multi_accept on;
}CF is under attack mode
-
I have chaneg nginx conf with :
worker_rlimit_nofile 70000;
events {
worker_connections 65535;
multi_accept on;
}CF is under attack mode
@DownPW I still have access to your Cloudflare tenant so will have a look shortly.
EDIT: I am in now - personally, I would also enable this (and configure it)
-
@DownPW I still have access to your Cloudflare tenant so will have a look shortly.
EDIT: I am in now - personally, I would also enable this (and configure it)
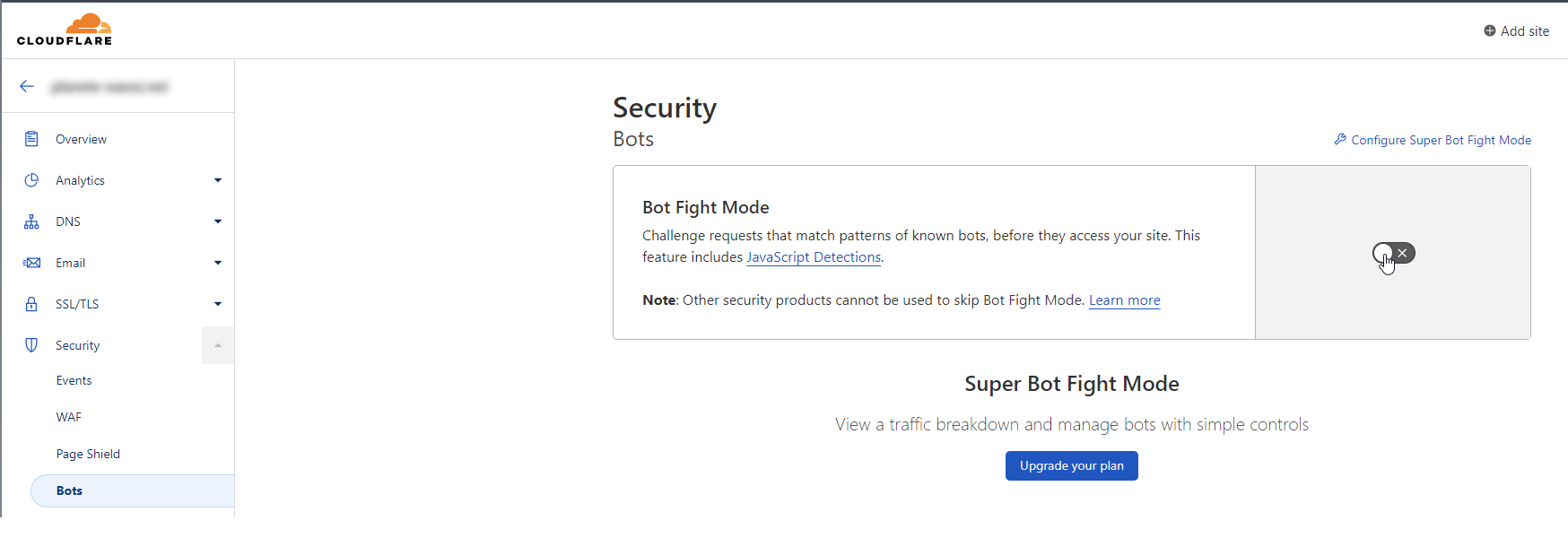
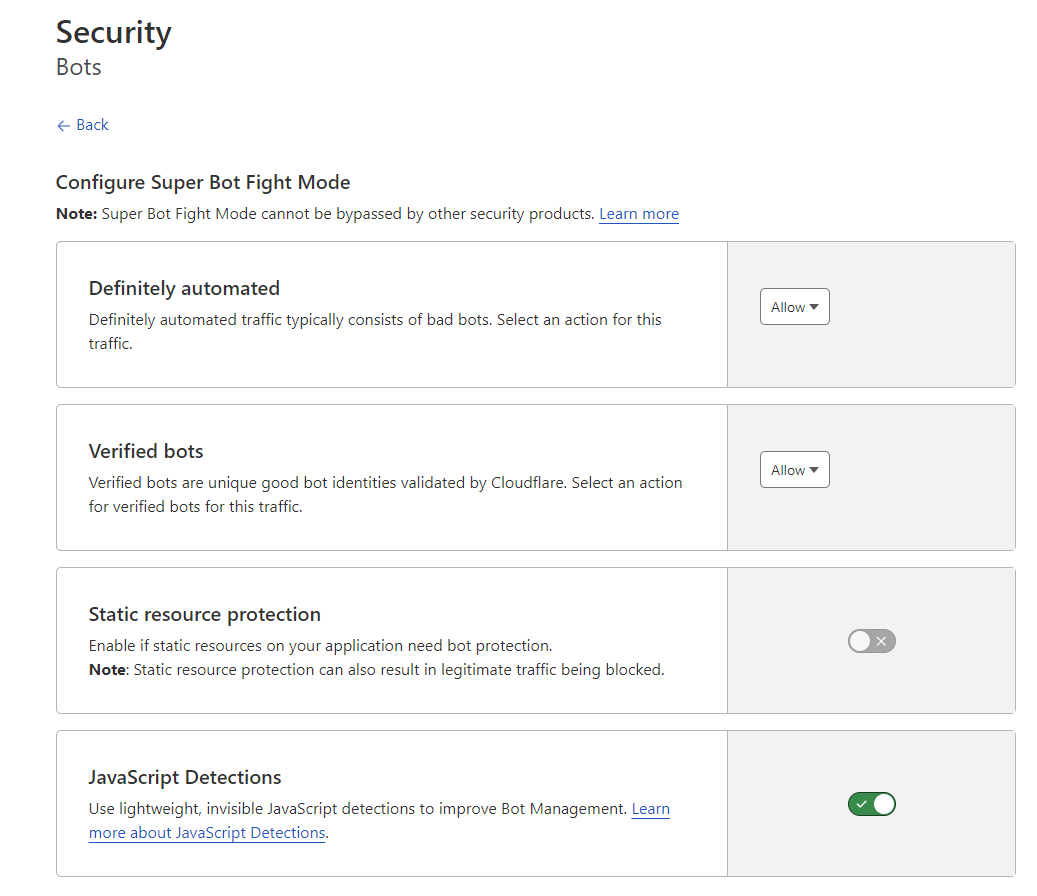
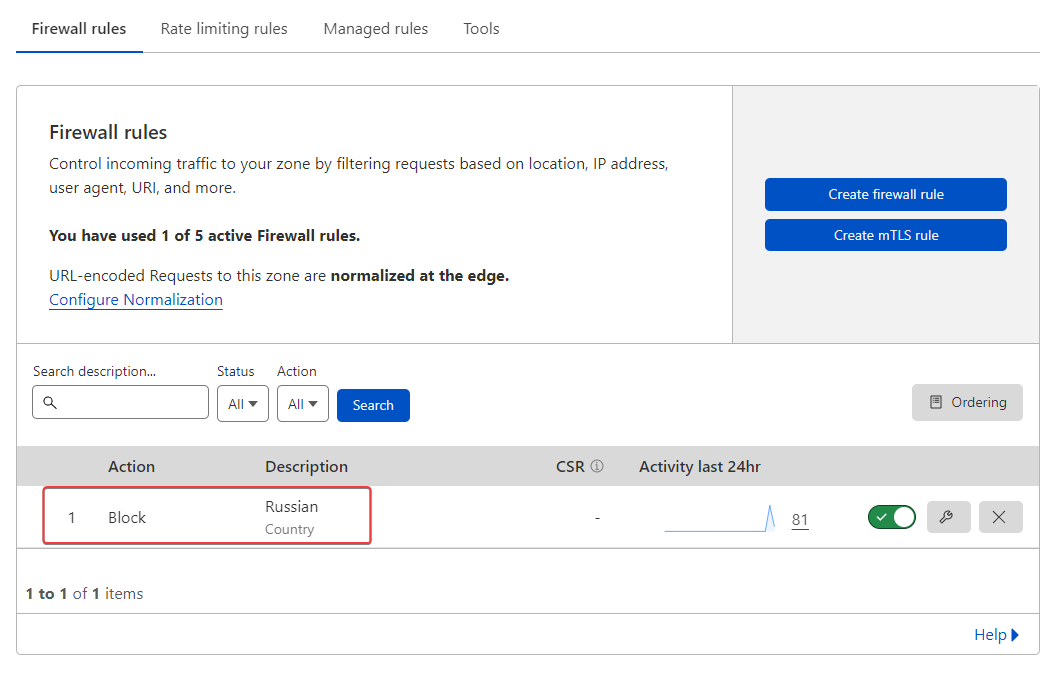
@phenomlab I have already activate it and add a waf rules for russian country
and this settings for ddos protection :
-
@phenomlab I have already activate it and add a waf rules for russian country
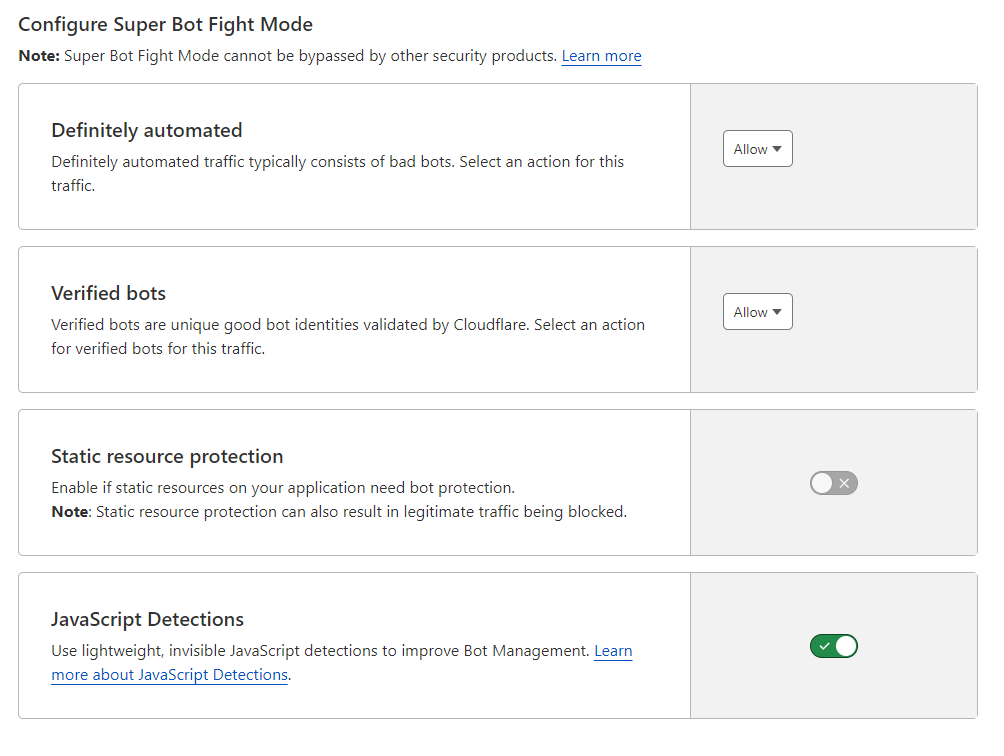
With this bots settings :
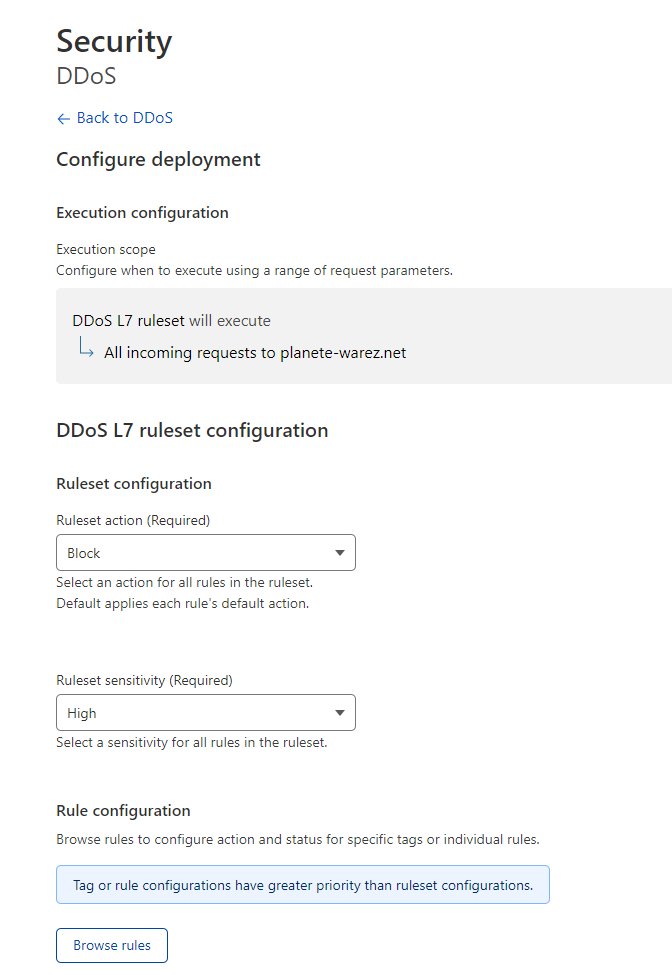
and this settings for ddos protection :
@DownPW said in NODEBB: Nginx error performance & High CPU:
I have already activate it
Are you sure? When I checked your tenant it wasn’t active - it’s from where I took the screenshot

-
@DownPW said in NODEBB: Nginx error performance & High CPU:
I have already activate it
Are you sure? When I checked your tenant it wasn’t active - it’s from where I took the screenshot

yep I activate it after

-
yep I activate it after

For your information @phenomlab ,
- I have ban via iptables suspicious ip address find on /etc/nginx/accesss.log and virtualhost access.log like this :
iptables -I INPUT -s IPADDRESS -j DROP - Activate bot option on CF
- Create contry rules (Russie and China) on CF WAF
- I left under attack mode option activated on CF
- I have just change nginx.conf like this for test (If you have best value, I take it ! ) :
worker_rlimit_nofile 70000; events { worker_connections 65535; multi_accept on; } http { ## # Basic Settings ## limit_req_zone $binary_remote_addr zone=flood:10m rate=100r/s; limit_req zone=flood burst=100 nodelay; limit_conn_zone $binary_remote_addr zone=ddos:10m; limit_conn ddos 100; 100r/s iit’s already a lot !!
and for vhost file :
server { ..... location / { limit_req zone=flood; #Test limit_conn ddos 100; #Test } –> If you have other ideas, I’m interested
–> If you have better values to use in what I modified, please let me know. - I have ban via iptables suspicious ip address find on /etc/nginx/accesss.log and virtualhost access.log like this :
-
For your information @phenomlab ,
- I have ban via iptables suspicious ip address find on /etc/nginx/accesss.log and virtualhost access.log like this :
iptables -I INPUT -s IPADDRESS -j DROP - Activate bot option on CF
- Create contry rules (Russie and China) on CF WAF
- I left under attack mode option activated on CF
- I have just change nginx.conf like this for test (If you have best value, I take it ! ) :
worker_rlimit_nofile 70000; events { worker_connections 65535; multi_accept on; } http { ## # Basic Settings ## limit_req_zone $binary_remote_addr zone=flood:10m rate=100r/s; limit_req zone=flood burst=100 nodelay; limit_conn_zone $binary_remote_addr zone=ddos:10m; limit_conn ddos 100;100r/s iit’s already a lot !!
and for vhost file :
server { ..... location / { limit_req zone=flood; #Test limit_conn ddos 100; #Test }–> If you have other ideas, I’m interested
–> If you have better values to use in what I modified, please let me know.@DownPW my only preference would be to not set
worker_connectionsso high - I have ban via iptables suspicious ip address find on /etc/nginx/accesss.log and virtualhost access.log like this :
-
Ok so what value do you advise?
-
Ok so what value do you advise?
@DownPW you should base it on the output of
ulimit- see belowWith that high value you run the risk of overwhelming your server.
Did this solution help you?
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (ether email, or push notification). You'll also be able to save bookmarks, use reactions, and upvote to show your appreciation to other community members.
With your input, this post could be even better 💗
RegisterLog in