Securing your webserver against common attacks
-
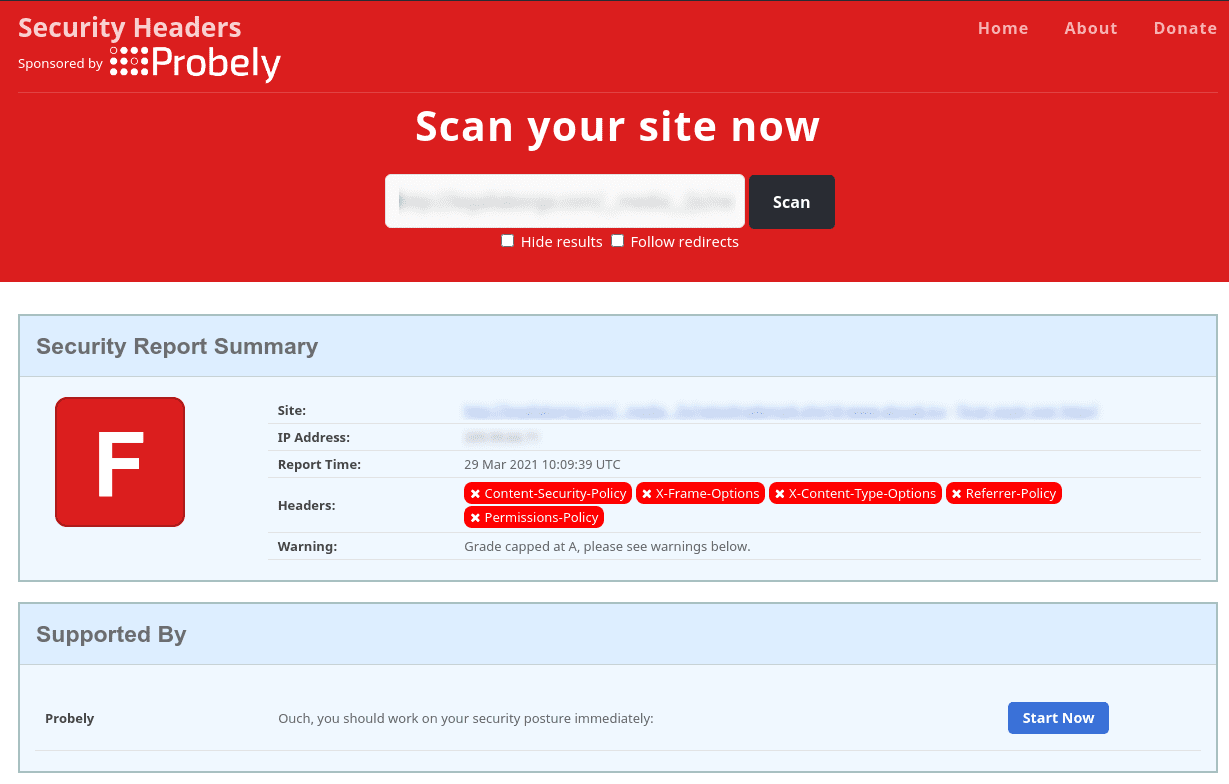
It surprises me (well, actually, dismays me in most cases) that new websites appear online all the time who have clearly spent an inordinate amount of time on cosmetics / appearance, and decent hosting, yet failed to address the elephant in the room when it comes to actually securing the site itself. Almost all the time, when I perform a quick security audit using something simple like the below
I often see something like this
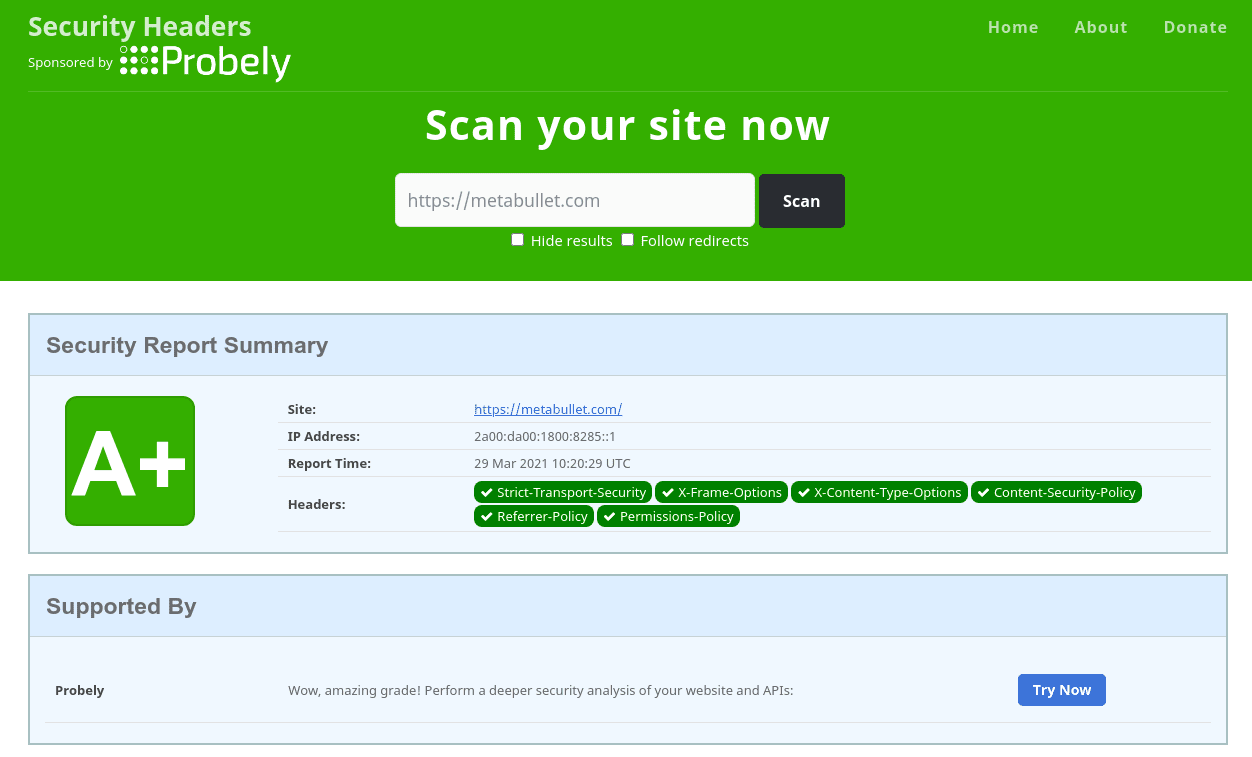
Not a pretty sight. Not only does this expose your site to unprecedented risk, but also looks bad when others decide to perform a simple (and very public) check. Worse still is the sheer number of so called “security experts” who claim to solve all of your security issues with their “silver bullet” solution (sarcasm intended), yet have neglected to get their own house in order. So that can you do to resolve this issue ? It’s actually much easier than it seems. Dependant on the web server you are running, you can include these headers.
Apache
<IfModule mod_headers.c> Header set X-Frame-Options "SAMEORIGIN" header set X-XSS-Protection "1; mode=block" Header set X-Download-Options "noopen" Header set X-Content-Type-Options "nosniff" Header set Content-Security-Policy "upgrade-insecure-requests" Header set Referrer-Policy 'no-referrer' add Header set Feature-Policy "geolocation 'self' https://yourdomain.com" Header set Permissions-Policy "geolocation=(),midi=(),sync-xhr=(),microphone=(),camera=(),magnetometer=(),gyroscope=(),fullscreen=(self),payment=()" Header set X-Powered-By "Whatever text you want to appear here" Header set Access-Control-Allow-Origin "https://yourdomain.com" Header set X-Permitted-Cross-Domain-Policies "none" Header set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload" </IfModule> NGINX
add_header X-Frame-Options "SAMEORIGIN" always; add_header X-XSS-Protection "1; mode=block"; add_header X-Download-Options "noopen" always; add_header X-Content-Type-Options "nosniff" always; add_header Content-Security-Policy "upgrade-insecure-requests" always; add_header Referrer-Policy 'no-referrer' always; add_header Feature-Policy "geolocation 'self' https://yourdomain.com" always; add_header Permissions-Policy "geolocation=(),midi=(),sync-xhr=(),microphone=(),camera=(),magnetometer=(),gyroscope=(),fullscreen=(self),payment=();"; add_header X-Powered-By "Whatever text you want to appear here" always; add_header Access-Control-Allow-Origin "https://yourdomain.com" always; add_header X-Permitted-Cross-Domain-Policies "none" always; add_header Strict-Transport-Security "max-age=63072000; includeSubdomains;" always; Note, that
https://yourdomain.comshould be changed to reflect your actual domain. This is just a placeholder to demonstrate how the headers need to be structured.Restart Apache or NGINX, and then perform the test again.
More detail around these headers can be found here
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (ether email, or push notification). You'll also be able to save bookmarks, use reactions, and upvote to show your appreciation to other community members.
With your input, this post could be even better 💗
RegisterLog in