Tips
Some useful articles that can easily get you out of that hole you might have just fell into…:)
10
Topics
85
Posts
Trending
Trending
I wanted to create a DEV instance of sudonix, so went ahead and registered sudonix.dev, installed NodeBB, then recovered the database.
All good - apart from the fact that I consistently got the dreaded csrf invalid message…
Here’s the log extract
2022-03-21T14:15:25.859Z [4571/91294] - info: Initializing NodeBB v1.19.5 https://sudonix.dev
2022-03-21T14:15:27.761Z [4571/91294] - info: [socket.io] Restricting access to origin: https://sudonix.dev:*
2022-03-21T14:15:27.858Z [4571/91294] - warn: [plugins] "@nodebb/nodebb-plugin-user-level" is active but not installed.
(node:91294) Warning: Accessing non-existent property 'padLevels' of module exports inside circular dependency
(Use `node --trace-warnings ...` to show where the warning was created)
2022-03-21T14:15:28.637Z [4571/91294] - warn: [plugins/load] DEPRECATION The hook filter:router.page has been deprecated as of v1.15.3, and slated for removal in v2.1.0. Please use response:router.page instead. The following plugins are still listening for this hook:
* nodebb-plugin-write-api
2022-03-21T14:15:28.724Z [4571/91294] - info: [plugins/spam-be-gone] Settings loaded
2022-03-21T14:15:28.734Z [4571/91294] - info: [reputation-rules] settings loaded
2022-03-21T14:15:28.925Z [4571/91294] - info: [api] Adding 4 route(s) to `api/v3/plugins`
2022-03-21T14:15:28.936Z [4571/91294] - info: [router] Routes added
2022-03-21T14:15:28.947Z [4571/91294] - info: NodeBB Ready
2022-03-21T14:15:28.948Z [4571/91294] - info: Enabling 'trust proxy'
2022-03-21T14:15:28.950Z [4571/91294] - info: NodeBB is now listening on: 0.0.0.0:4571
2022-03-21T14:15:47.488Z [4571/91294] - error: [plugin/iframely] Could not parse embed: Failed to lookup view "partials/iframely-widget-card" in views directory "/home/sudonix.dev/nodebb/build/public/templates". Url: https://sudonix.com/topic/233/nodebb-welcome-message-with-logo-footer-change/3?_=1645445273209
Missing translation "2factor:title" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_unsolved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:topic_solved" for language "en-GB"
Missing translation "qanda:menu.solved" for language "en-GB"
Missing translation "qanda:menu.solved" for language "en-GB"
2022-03-21T14:15:48.899Z [4571/91294] - error: POST /logout
invalid csrf token
Tried clearing cache, no dice. Tried incognito mode, no dice.
After some significant head scratching, it suddenly dawned on me that the cookie domain would need to be reset as this is a PROD database replica in a new domain.
To do this.
Open the mondogb console
Select your database - in my case use sudonixdev;
Issue this command db.objects.update({_key: "config"}, {$set: {cookieDomain: ""}});
Restart nodebb
Problem solved - able to login
Tips
27 Nov 2024, 23:09
Tips
29 Sept 2024, 20:48
Managing videos is a big hassle. To follow the 3-2-1 backup strategy, I want to keep a copy of my videos online. After some research, I found that GoPro is the easiest and cheapest option, costing around $25 or $50 per year for unlimited footage. (i have 20TB videos)Now, the goal is to upload all my files to GoPro.
GoPro doesn’t provide a drive-like system, so I need to upload files directly to the GoPro website. Before doing that, I want to add folder names to the file names using a Linux command to rename them. so i can use their search to find files later.
All my videos are stored in Synology Drive in the following format:
Videos/date/filename1.mp4
I only want to rename the MP4 files to have the format date-filename1.mp4. How can I do this using a command targeting all directory and subdirectories?
Tips
13 Dec 2023, 11:19
Tips
7 Jul 2023, 17:40
Tips
21 Jun 2023, 22:26
Tips
6 Apr 2023, 10:06
Tips
14 Mar 2023, 15:02
Tips
6 Feb 2023, 19:37
Not everyone can afford expensive operational monitoring tools, so here’s a cheap and dirty way to use cURL to scrape a webpage, return it’s status, and then compare it with the value you’d get if the page was up. If that doesn’t match, we assume the page is down, and then trigger an email as an alarm.
#!/bin/bash
CURLOPT_SSL_VERIFYPEER => 0
# Your site URL goes here
website="https://your.forum.url*";
result=$(curl -m 60 -Is $website | head -n 1 | tr -d "\r")
# note that this value varies depending on platform. You should echo $result to see what the correct value is when querying the site itself when you know it's running.
expecting="HTTP/2 200";
timestamp=$(date);
if [ "$result" = "$expecting" ];
then
output="$timestamp -> $website $result -> Website UP";
echo $output;
echo $output >> /path/to/your/logfile/log.txt
else
output="$timestamp -> $website $result -> Website DOWN";
echo $output;
echo $output >> /path/to/your/logfile/log.txt
# Fire an alert as the result isn't what we expected
mailbody="$output"
echo "From: email@domain.com" > /tmp/mail.tmp
echo "To: email@domain.com" >> /tmp/mail.tmp
echo "Subject: ALERT: Website $website is DOWN" >> /tmp/mail.tmp
echo "" >> /tmp/mail.tmp
echo $mailbody >> /tmp/mail.tmp
cat /tmp/mail.tmp | /usr/sbin/sendmail -t -f "email@domain.com"
fi
This is very primitive, but works very well. Note, that sendmail is being used here to trigger an email. If you do not have that, you’ll need to substitute the path and command for whatever you want to use.
Have fun…
Tips
19 Sept 2022, 04:03
With today’s modern world where we should all be using password managers and authentication apps to further enhance our online security presence, it’s easy to fall into the trap of not being able to recover Google Authenticator if your device is lost or stolen.
Whilst this sounds like a “it won’t happen to me”, never say never. Mobile devices are highly sought after in today’s world, and given that virtually everything we do online is from a mobile phone or tablet, it’s easy to become complacent. Sure, it’s available immediately if you need it, but what if you lose it ?
What could happen ?
Well, for one, you’ll be without your device meaning that if you rely on that same peripheral to access a password manager, or generate TOTP based 6 digit codes, you’re going to be in something of a “hole” to say the least. You can get access to most password managers via an online vault, but if that account you need to access was secured with 2FA or push authentication, and you no longer have the associated device, then you’re in for quite a rough ride without a means of recovery.
This is where (for example, but not limited to) Google Authenticator will make you immediately fall on your sword if you don’t have copies of the backup codes, or the secure password seed used to create the pairing in the first place. Be honest - do you keep a record of backup codes ? I’m guessing you don’t
It’s not actually possible to quickly and easily backup Google Authenticator, or the codes generated by it. It’s a simple process to transfer to another phone, but ONLY if you have the old device. If your phone or tablet is lost or stolen, and you have no means of proving who you are, then you are, for want of a better phrase, royally screwed.
The Solution
DON’T rely on Google Authenticator. Yes, it’s free. Yes, it’s simple, but if you lose your device, then you’ll quickly find out just how much of an inconvenience this is. I switched away from Google Authenticator years ago in favor of AUTHY (now known as Twillo). Not only can you have multiple devices, but there is a recovery mechanism whereby you can get access to your data on another device by simply going through the recovery process. The one caveat here is that the recovery requests need to be manually reviewed and approved.
I went through this same exercise around 4 years ago when my phone literally froze up, then died. I sent the phone back to the manufacturer who informed me that the device was completely dead (it was an LG - never again) and that they would be shipping a replacement. Great, but what about the 2FA codes etc ? As it’s an Android device, I simply pulled all of the settings back from my Google Account. However, getting the codes back into AUTHY meant I needed to go through the recovery steps.
These are pretty simple, but you need to be able to answer security questions in order to proceed. Another great addition in AUTHY is that you are periodically requested to enter the backup passcode so that backups of all your accounts can easily be taken
A bit more information around that can be found here
https://support.authy.com/hc/en-us/articles/115012672088-Restoring-Authy-Access-on-a-New-Lost-or-Inaccessible-Phone
And here
https://shieldplanet.com/what-if-i-lose-my-phone-with-google-authenticator-on-it/
This article is from the same bunch who developed the Shield Security plugin for WordPress, and they provide the same stark warning as I do here
https://getshieldsecurity.com/blog/google-authenticator-backups/
Transferring out of Google Authenticator is a simple process, but requires re-enrolling your device via AUTHY (or another product) in each application or account you have secured.
BitWarden and others have the ability to incorporate 2FA generation and security in their password manager apps for mobile devices. The huge benefit here is that this is replicated into the online vault, meaning the codes are also generated there, and you can still access your accounts without your phone. More info about that here
https://bitwarden.com/help/authenticator-keys/
Don’t get caught out by sticking with Google Authenticator
Tips
29 Aug 2022, 11:17
-
Invalid CSRF on dev install
Watching Ignoring Scheduled Pinned Locked Moved Solved csrf 21 Mar 2022, 15:115 Votes10 Posts5k Views -
Adding a banner to chat messages
Watching Ignoring Scheduled Pinned Locked Moved banner custom 18 Jul 2023, 13:05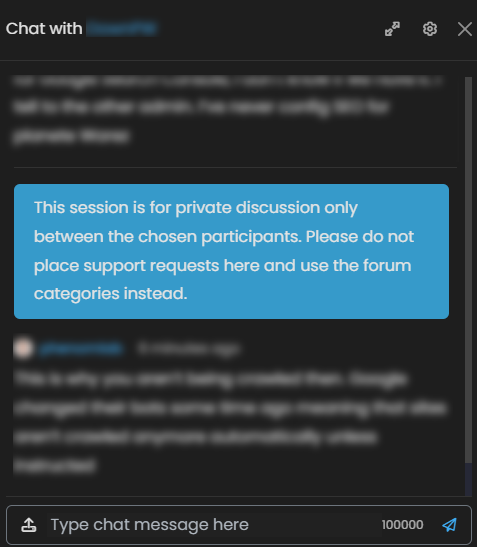 1
17 Votes37 Posts3k Views
1
17 Votes37 Posts3k Views -
Rename videos in bulk - linux commands
Watching Ignoring Scheduled Pinned Locked Moved Unsolved gopro linux commands 10 Dec 2023, 09:354 Votes12 Posts1k Views -
Unable to change icon in NodeBB navigation
Watching Ignoring Scheduled Pinned Locked Moved navigation nodebb 7 Jul 2023, 17:40 7
1 Votes1 Posts261 Views
7
1 Votes1 Posts261 Views -
Google slow to crawl website (Search Console)
Watching Ignoring Scheduled Pinned Locked Moved seo crawl google 20 Jun 2023, 11:02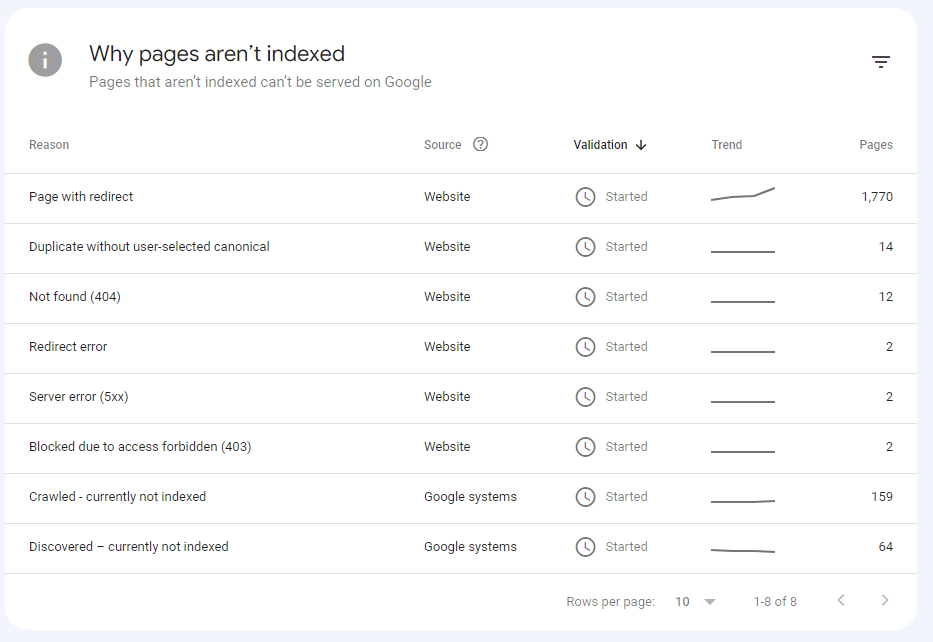 1
3 Votes6 Posts605 Views
1
3 Votes6 Posts605 Views -
Which is Better Samsung S23 or Xiaomi 13
Watching Ignoring Scheduled Pinned Locked Moved xiaomi 13 samsung s23 3 Apr 2023, 20:043 Votes5 Posts463 Views -
View / terminate multiple instances of a process in Windows
Watching Ignoring Scheduled Pinned Locked Moved taskkill processes windows 28 Feb 2023, 11:01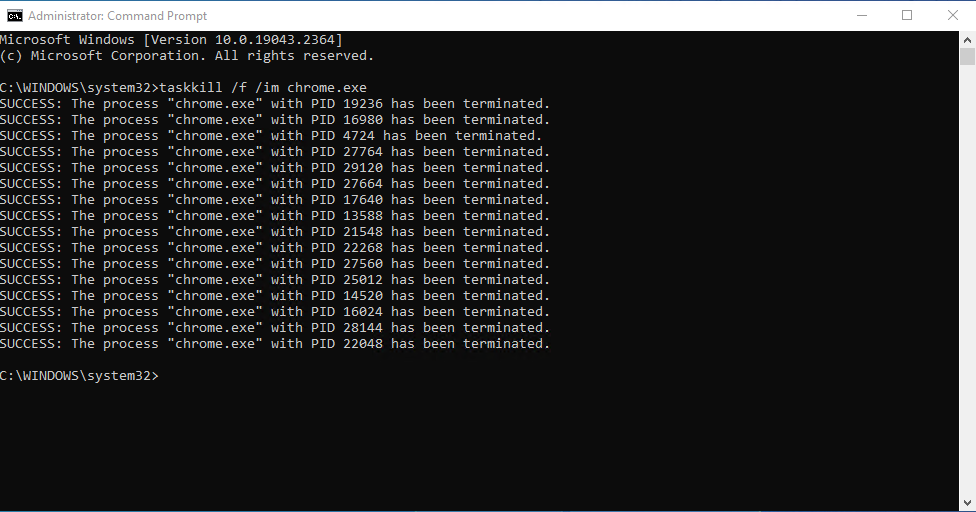 1
2 Votes2 Posts458 Views
1
2 Votes2 Posts458 Views -
Killing Linux Zombie Processes
Watching Ignoring Scheduled Pinned Locked Moved zombie linux 6 Feb 2023, 15:01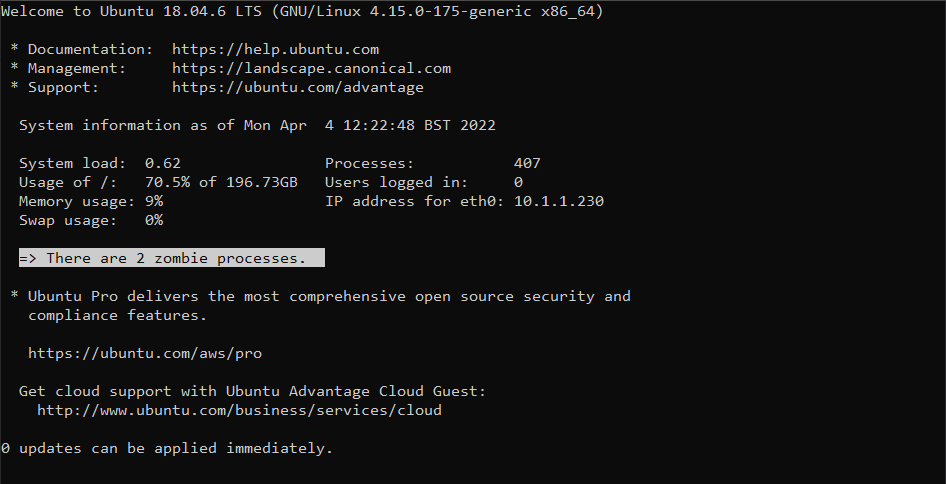 7
2 Votes3 Posts487 Views
7
2 Votes3 Posts487 Views -
Simple bash website monitoring script
Watching Ignoring Scheduled Pinned Locked Moved monitoring 16 Sept 2022, 13:014 Votes2 Posts470 Views -
Google Authenticator for 2FA
Watching Ignoring Scheduled Pinned Locked Moved tips 2fa 24 Aug 2022, 12:376 Votes7 Posts763 Views