Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix
-
no Hetzner firewall configured
no crowdsecI have just firewalld of virtualmin by default. I have add 25 and 587 port. Same problem
other log :
Feb 20 21:40:11 adm postfix/smtpd[679903]: disconnect from unknown[45.129.14.179] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:40:11 adm postfix/smtpd[679903]: warning: unknown[45.129.14.179]: SASL LOGIN authentication failed: authentication failure Feb 20 21:40:05 adm postfix/smtpd[679903]: connect from unknown[45.129.14.179] Feb 20 21:40:05 adm postfix/smtpd[679903]: warning: hostname 179.hosted-by.198xd.com does not resolve to address 45.129.14.179 Feb 20 21:39:54 adm postfix/smtpd[679911]: disconnect from unknown[45.129.14.179] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:54 adm postfix/smtpd[679911]: warning: unknown[45.129.14.179]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:50 adm postfix/smtpd[679903]: disconnect from unknown[45.129.14.128] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:50 adm postfix/smtpd[679903]: warning: unknown[45.129.14.128]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:47 adm postfix/smtpd[679911]: connect from unknown[45.129.14.179] Feb 20 21:39:47 adm postfix/smtpd[679911]: warning: hostname 179.hosted-by.198xd.com does not resolve to address 45.129.14.179 Feb 20 21:39:39 adm postfix/smtpd[679903]: connect from unknown[45.129.14.128] Feb 20 21:39:39 adm postfix/smtpd[679903]: warning: hostname 128.hosted-by.198xd.com does not resolve to address 45.129.14.128 Feb 20 21:39:38 adm postfix/smtpd[679911]: disconnect from unknown[45.129.14.179] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:37 adm postfix/smtpd[679911]: warning: unknown[45.129.14.179]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:32 adm postfix/smtpd[679903]: disconnect from unknown[45.129.14.128] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:32 adm postfix/smtpd[679903]: warning: unknown[45.129.14.128]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:30 adm postfix/smtpd[679911]: connect from unknown[45.129.14.179] Feb 20 21:39:30 adm postfix/smtpd[679911]: warning: hostname 179.hosted-by.198xd.com does not resolve to address 45.129.14.179 Feb 20 21:39:24 adm postfix/smtpd[679903]: connect from unknown[45.129.14.128] Feb 20 21:39:24 adm postfix/smtpd[679903]: warning: hostname 128.hosted-by.198xd.com does not resolve to address 45.129.14.128 Feb 20 21:39:22 adm postfix/smtp[679066]: 1AD316278E: to=<xxxxxxxxxxxx@gmail.com>, relay=none, delay=3410, delays=3260/0.03/150/0, dsn=4.4.1, status=deferred (connect to alt2.gmail-smtp-in.l.google.com[2a00:1450:4025:c03::1a]:25: Connection timed out) Feb 20 21:39:22 adm postfix/smtp[679066]: connect to alt2.gmail-smtp-in.l.google.com[2a00:1450:4025:c03::1a]:25: Connection timed out Feb 20 21:39:19 adm postfix/smtpd[679911]: disconnect from unknown[45.129.14.179] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:19 adm postfix/smtpd[679911]: warning: unknown[45.129.14.179]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:17 adm postfix/smtpd[679903]: disconnect from unknown[45.129.14.128] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:16 adm postfix/smtpd[679903]: warning: unknown[45.129.14.128]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:12 adm postfix/smtpd[679911]: connect from unknown[45.129.14.179] Feb 20 21:39:12 adm postfix/smtpd[679911]: warning: hostname 179.hosted-by.198xd.com does not resolve to address 45.129.14.179 Feb 20 21:39:08 adm postfix/smtpd[679903]: connect from unknown[45.129.14.128] Feb 20 21:39:08 adm postfix/smtpd[679903]: warning: hostname 128.hosted-by.198xd.com does not resolve to address 45.129.14.128 Feb 20 21:39:02 adm postfix/smtpd[679911]: disconnect from unknown[45.129.14.179] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:01 adm postfix/smtpd[679911]: warning: unknown[45.129.14.179]: SASL LOGIN authentication failed: authentication failure Feb 20 21:39:01 adm postfix/smtpd[679903]: disconnect from unknown[45.129.14.128] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:39:00 adm postfix/smtpd[679903]: warning: unknown[45.129.14.128]: SASL LOGIN authentication failed: authentication failure Feb 20 21:38:55 adm postfix/smtpd[679911]: connect from unknown[45.129.14.179] Feb 20 21:38:55 adm postfix/smtpd[679911]: warning: hostname 179.hosted-by.198xd.com does not resolve to address 45.129.14.179 Feb 20 21:38:53 adm postfix/smtpd[679903]: connect from unknown[45.129.14.128] Feb 20 21:38:53 adm postfix/smtpd[679903]: warning: hostname 128.hosted-by.198xd.com does not resolve to address 45.129.14.128 Feb 20 21:38:52 adm postfix/smtp[679066]: connect to alt1.gmail-smtp-in.l.google.com[2a00:1450:4013:c16::1b]:25: Connection timed out Feb 20 21:38:44 adm postfix/smtpd[679903]: disconnect from unknown[45.129.14.128] ehlo=1 auth=0/1 rset=1 quit=1 commands=3/4 Feb 20 21:38:43 adm postfix/smtpd[679903]: warning: unknown[45.129.14.128]: SASL LOGIN authentication failed: authentication failure Feb 20 21:38:38 adm postfix/smtpd[679903]: connect from unknown[45.129.14.128] Feb 20 21:38:38 adm postfix/smtpd[679903]: warning: hostname 128.hosted-by.198xd.com does not resolve to address 45.129.14.128 Feb 20 21:38:22 adm postfix/smtp[678126]: 73987627BE: to=<xxxxxxxxxxxxxxxxxxxxxxxx@gmail.com>, relay=none, delay=3350, delays=3200/0.03/150/0, dsn=4.4.1, status=deferred (connect to alt2.gmail-smtp-in.l.google.com[2a00:1450:4025:c03::1a]:25: Connection timed out) Feb 20 21:38:22 adm postfix/smtp[678126]: connect to alt2.gmail-smtp-in.l.google.com[2a00:1450:4025:c03::1a]:25: Connection timed out Feb 20 21:38:22 adm postfix/smtp[679066]: connect to alt1.gmail-smtp-in.l.google.com[142.250.153.26]:25: Connection timed out Feb 20 21:37:52 adm postfix/smtp[678126]: connect to alt1.gmail-smtp-in.l.google.com[2a00:1450:4013:c16::1b]:25: Connection timed out Feb 20 21:37:52 adm postfix/error[679677]: 20D20627C1: to=<xxxxxxxxxxxxxxx@caramail.com>, relay=none, delay=5027, delays=4967/60/0/0.01, dsn=4.4.1, status=deferred (delivery temporarily suspended: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out) Feb 20 21:37:52 adm postfix/error[679676]: 225BB627B7: to=<xxxxxxxxxxxxxxxxx@caramail.com>, relay=none, delay=3784, delays=3724/60/0/0, dsn=4.4.1, status=deferred (delivery temporarily suspended: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out) Feb 20 21:37:52 adm postfix/smtp[679070]: 1ED2A627AB: to=<xxxxxxxxxxxxxxxx@caramail.com>, relay=none, delay=4432, delays=4372/0.08/60/0, dsn=4.4.1, status=deferred (connect to mx00.caramail.com[212.227.15.30]:25: Connection timed out) Feb 20 21:37:52 adm postfix/smtp[679070]: connect to mx00.caramail.com[212.227.15.30]:25: Connection timed out Feb 20 21:37:52 adm postfix/error[679676]: 1FBDB627B3: to=<xxxxxxxxxxxxxxxx@caramail.com>, relay=none, delay=3500, delays=3440/60/0/0.01, dsn=4.4.1, status=deferred (delivery temporarily suspended: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out) Feb 20 21:37:52 adm postfix/smtp[679069]: 1DE7B62796: to=<xxxxxxxxxxxxxx@caramail.com>, relay=none, delay=4587, delays=4527/0.07/60/0, dsn=4.4.1, status=deferred (connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out) Feb 20 21:37:52 adm postfix/smtp[679068]: 1D536627AE: to=<xxxxxxxxxxxxxxxx@caramail.com>, relay=none, delay=4531, delays=4471/0.05/60/0, dsn=4.4.1, status=deferred (connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out) Feb 20 21:37:52 adm postfix/smtp[679067]: 1C5D3627B6: to=<xxxxxxxxxxxxxxxxxxx@caramail.com>, relay=none, delay=3815, delays=3755/0.04/60/0, dsn=4.4.1, status=deferred (connect to mx00.caramail.com[212.227.15.30]:25: Connection timed out) Feb 20 21:37:52 adm postfix/smtp[679069]: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out Feb 20 21:37:52 adm postfix/smtp[679068]: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out Feb 20 21:37:52 adm postfix/smtp[679067]: connect to mx00.caramail.com[212.227.15.30]:25: Connection timed out Feb 20 21:37:52 adm postfix/smtp[679066]: connect to gmail-smtp-in.l.google.com[142.250.110.27]:25: Connection timed out Feb 20 21:37:22 adm postfix/smtp[678126]: connect to alt1.gmail-smtp-in.l.google.com[142.250.153.26]:25: Connection timed out Feb 20 21:37:22 adm postfix/smtp[679070]: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out Feb 20 21:37:22 adm postfix/smtp[679069]: connect to mx00.caramail.com[212.227.15.30]:25: Connection timed out Feb 20 21:37:22 adm postfix/smtp[679068]: connect to mx00.caramail.com[212.227.15.30]:25: Connection timed out Feb 20 21:37:22 adm postfix/smtp[679067]: connect to mx01.caramail.com[217.72.192.76]:25: Connection timed out Feb 20 21:37:22 adm postfix/smtp[679066]: connect to gmail-smtp-in.l.google.com[2a00:1450:400c:c0b::1b]:25: Connection timed out Feb 20 21:37:05 adm postfix/anvil[677271]: statistics: max cache size 3 at Feb 20 21:27:30 Feb 20 21:37:05 adm postfix/anvil[677271]: statistics: max connection count 1 for (smtp:45.88.90.174) at Feb 20 21:27:05 Feb 20 21:37:05 adm postfix/anvil[677271]: statistics: max connection rate 4/60s for (smtp:45.129.14.128) at Feb 20 21:28:06 Feb 20 21:36:52 adm postfix/smtp[678126]: connect to gmail-smtp-in.l.google.com[142.250.110.27]:25: Connection timed out -
-
@phenomlab said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
By default, Virtualmin based domains have email which is accessible at https://yourserver.com:20000
hmmm acess seem to work, I log with root but Inbox doesn’t seem to load correctly.
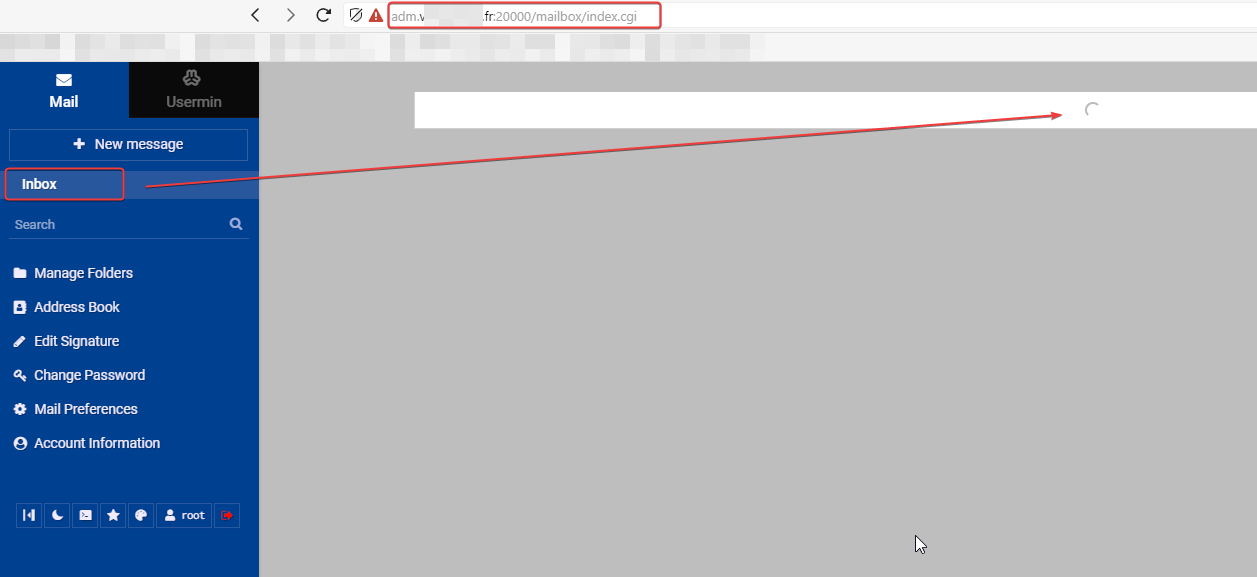
After a moment I have this message :
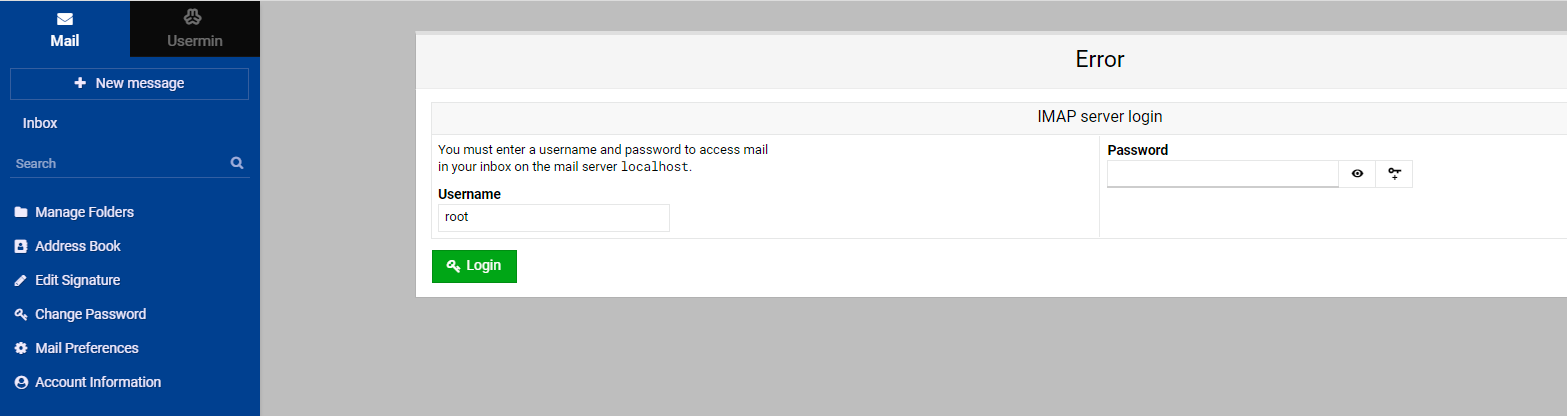
If I log with my root account like always, I have this :
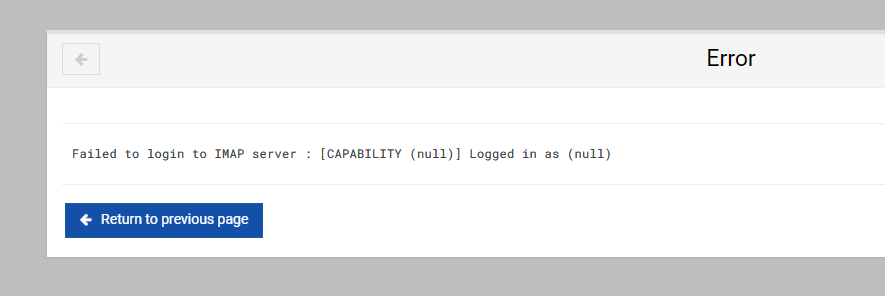
EDIT: seems Ok with other account. Seems root account doesn’t have inbox
@phenomlab said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
The MX record root.phenomlab.com is my VPS server
what is root.phenomlab.com on your virtualmin? it’s not a virtual server, jsut your hostname i guess
For example, I am login to virtualmin on adm.xxxx.fr (hostname of my server) so my mx field should be adm.xxxx.fr and not root.xxxx.fr right?
for dmarc and dkim, i’am not see for the moment, i see later
— EDIT:
my Dmarc configuration
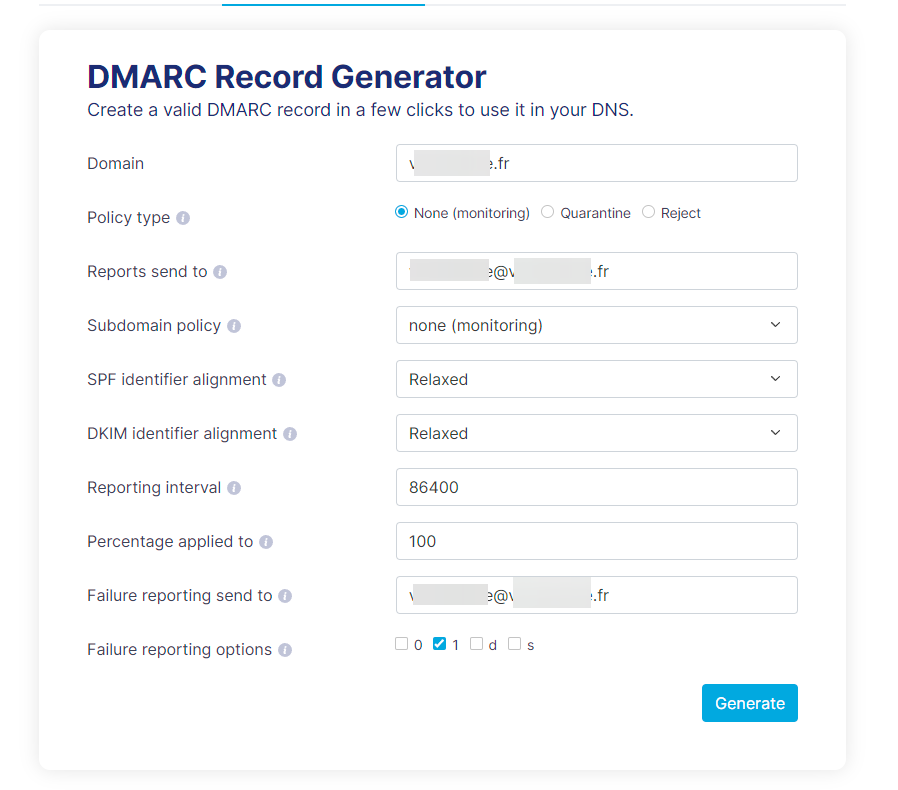
@DownPW said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
For example, I am login to virtualmin on adm.xxxx.fr (hostname of my server) so my mx field should be adm.xxxx.fr and not root.xxxx.fr right?
Yes, correct.
@DownPW said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
For DKIM, I don’t quite understand. Once generated in the tools you gave, I understand for the DNS entry in CF but what do I do with the private and public key?
The private and public key can simply be stored. You do not have to do anything with these.
-
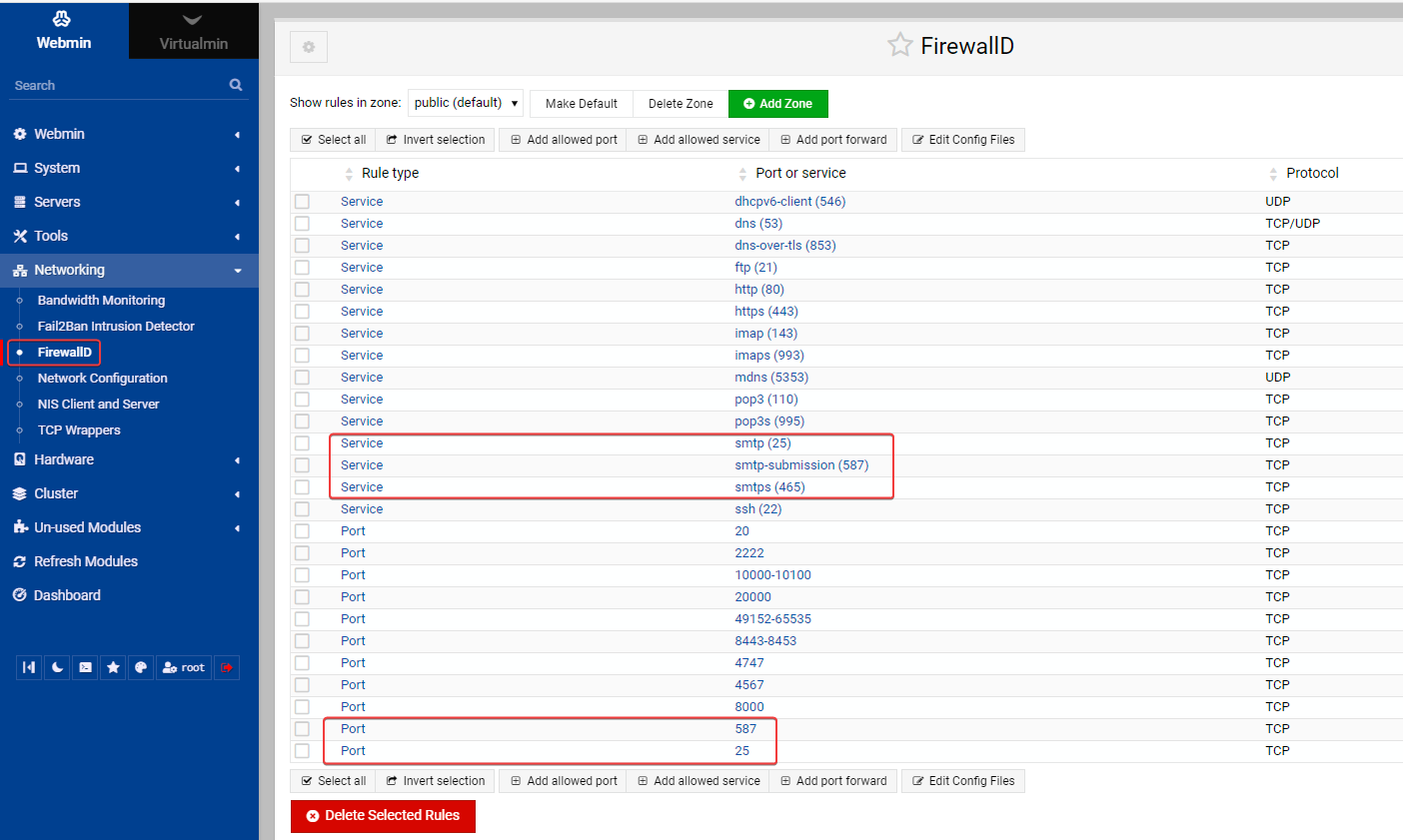
@DownPW said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
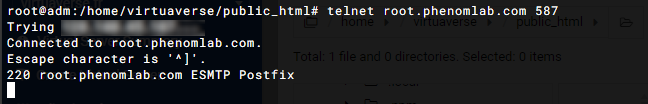
Seems port 25 OK
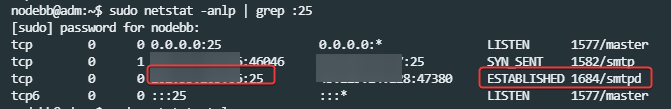
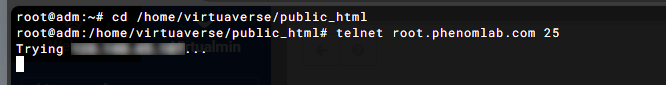
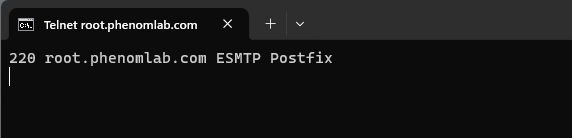
Not sure about that - see below from your server. When sending a
telnetrequest on port 25, there is no response. This typically means the port is closed on your side.What SHOULD happen is this
However, it DOES respond on port 587
From recollection, your VPS is being hosted by Hetzner. Although you have no firewall rules in place to prevent outbound connections on port 25, Hetzner by default will block this port until you’ve paid at least one month’s billing, and will only release the block if you formally request it. You’ll need to get the port unblocked before you can proceed - see below
Unfortunately, email spammers and scammers like to use cloud hosting providers. And we at Hetzner naturally want to prevent this. That’s why we block ports 25 and 465 by default on all cloud servers. This is a very common practice in the cloud hosting industry because it prevents abuse. We want to build trust with our new customers before we unblock these mail ports. Once you have been with us for a month and paid your first invoice, you can create a limit request to unblock these ports for a valid use case. In your request, you can tell us details about your use case. We make decisions on a case-by-case basis.
As an alternative, you can also use port 587 to send emails via external mail delivery services. Port 587 is not blocked and can be used without sending a limit request.
-
OUPS

Ok so I think it’s Hetzner who is blocking.
I will make them an unblocking request. -
OUPS

Ok so I think it’s Hetzner who is blocking.
I will make them an unblocking request.@DownPW Yep

-
-
Indeed. +1 for telnet.
I just trusted the netstats which told me that everything is OK which is certainly the case on the server.
since I didn’t have Telnet on hand I tested a website which told me OK

@DownPW said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
since I didn’t have Telnet on hand I tested a website which told me OK
I have to confess, I installed the
telnet-clienton your server for diagnostic purposes. -
OUPS

Ok so I think it’s Hetzner who is blocking.
I will make them an unblocking request.@DownPW said in Tutorial for secure emailing with personal domain,Cloudflare, virtualmin and postfix:
I will make them an unblocking request.
Curious to know how you got on with this…
-
sorry for the late response my friends. They unblocked port 25 very quickly and I can send emails;
Just that the domains in caramail.com refused my sending of email for obscure reasons and protonmail, I receive them but in spam with an error message
I will share all its errors with you to see and I would like to deepen that the DMARC, and DKIM puts the private/public key which I do not really understand (see my request above)
-
sorry for the late response my friends. They unblocked port 25 very quickly and I can send emails;
Just that the domains in caramail.com refused my sending of email for obscure reasons and protonmail, I receive them but in spam with an error message
I will share all its errors with you to see and I would like to deepen that the DMARC, and DKIM puts the private/public key which I do not really understand (see my request above)
@DownPW emails are going to junk because of missing DNS records as I mentioned previously. You won’t need to use the public and private keys unless you need extended and/or advanced functions.
-
-
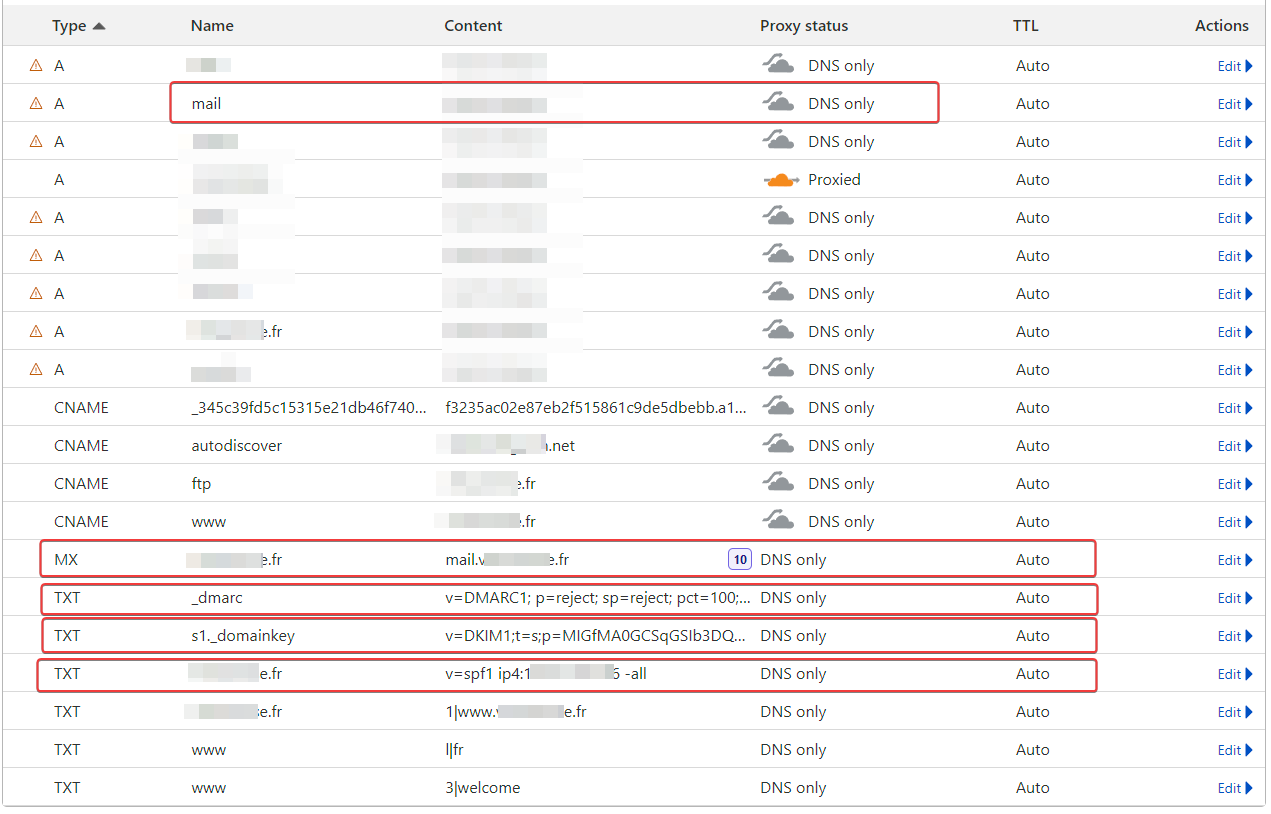
@DownPW not all are there. The
SPFrecord is missing. That’s enough to place email you sent into junk at the recipient end. -
Spf is on the screenshot
-
@DownPW sorry, yes, it is. Completely missed that.
-
@DownPW Can you PM me your domain name so I can run a few tests?
-
Yep no problem
-
@DownPW thanks. See PM. You can validate your domain in terms of its email suitability by using the checker below
In addition, there are some great generators and checkers here
-
@DownPW any update?
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (ether email, or push notification). You'll also be able to save bookmarks, use reactions, and upvote to show your appreciation to other community members.
With your input, this post could be even better 💗
RegisterLog in