Uber breached
-
In the news are several reports that Uber has once again become the victim of a large scale (this time with extremely wide ranging implications) attack on it’s internal network infrastructure. One security vendor has already described the breach as by far more extensive than the 2016 global incident (which impacted all of Uber’s entities).
The hacker, who claimed to be 18 years old, told NYT he had sent a text message to an Uber employee and was able to persuade the staff member to reveal a password after claiming to be a corporate information technology employee. The relatively simple social engineering hack allowed him to breach Uber’s systems, with the hacker describing the company’s security posture as weak. The huge gain from the perspective of any bad actor is that the level of access obtained is typically referred to as “god mode” (gamers might be familiar with this phrase, making your character invincible via a number of cheats). Essentially, this is much like an “access all areas” pass with absolutely no locked doors, or any area off limits in terms of Uber’s internal network infrastructure.
The real problem with “god mode” is that it allows the holder to assume complete control over systems without addition challenge, and essentially, lock out the original owner (Denial of Service) – basically, a complete compromise. If you’ve seen Die Hard 2, then you may remember that the plot involved an attack on Dulles Tower where all of the runways, flight management systems, and radar etc. were in full control of a remote entity who’d setup communication links in the adjacent church with the real tower being completely powerless whilst sea level was re-calibrated to minus 200ft causing a landing plane to hit the runway far earlier than they anticipated. Clearly, this is all very “Hollywood” – although it’s 100% feasible as the Uber breach has easily demonstrated and proved.
The impact on Uber is unimaginable – to the extent where they have been forced to close all internal systems whilst a full analysis of the breach is conducted, with the confidence and trust severely damaged from any client perspective.
The success of this attack highlights the increasing importance of awareness around Social Engineering. Through a myriad of techniques, a complete stranger was able to coerce an Uber employee with system admin access to accept the “push request” on his cell requesting access. Evidently, we was told (quite unbelievably) that the requests would stop if he accepted the request. Once he accepted, this effectively gave the remote attacker complete control. I fully expect the ripple effect of this attack to be felt for some considerable time with stolen financial records no doubt finding their way into the hands of those willing to use them for their own personal gain.
Everyone should be aware of the risks that impersonation attempts pose, and it is for this reason that you should always question any access request outside of the expected audience. If it doesn’t look or feel right, or the language used doesn’t match that particular person being impersonated, do not provide the access.
-
In the news are several reports that Uber has once again become the victim of a large scale (this time with extremely wide ranging implications) attack on it’s internal network infrastructure. One security vendor has already described the breach as by far more extensive than the 2016 global incident (which impacted all of Uber’s entities).
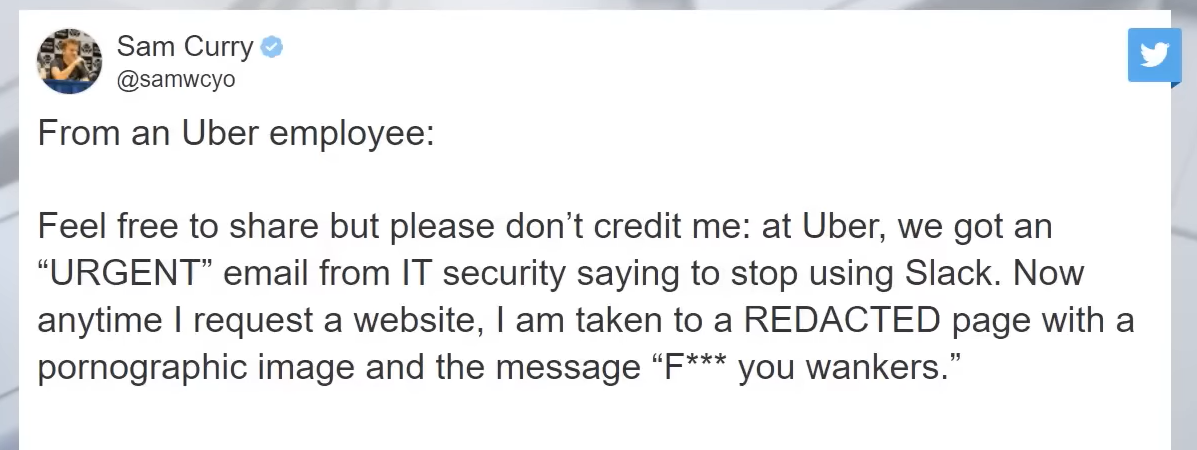
The hacker, who claimed to be 18 years old, told NYT he had sent a text message to an Uber employee and was able to persuade the staff member to reveal a password after claiming to be a corporate information technology employee. The relatively simple social engineering hack allowed him to breach Uber’s systems, with the hacker describing the company’s security posture as weak. The huge gain from the perspective of any bad actor is that the level of access obtained is typically referred to as “god mode” (gamers might be familiar with this phrase, making your character invincible via a number of cheats). Essentially, this is much like an “access all areas” pass with absolutely no locked doors, or any area off limits in terms of Uber’s internal network infrastructure.
The real problem with “god mode” is that it allows the holder to assume complete control over systems without addition challenge, and essentially, lock out the original owner (Denial of Service) – basically, a complete compromise. If you’ve seen Die Hard 2, then you may remember that the plot involved an attack on Dulles Tower where all of the runways, flight management systems, and radar etc. were in full control of a remote entity who’d setup communication links in the adjacent church with the real tower being completely powerless whilst sea level was re-calibrated to minus 200ft causing a landing plane to hit the runway far earlier than they anticipated. Clearly, this is all very “Hollywood” – although it’s 100% feasible as the Uber breach has easily demonstrated and proved.
The impact on Uber is unimaginable – to the extent where they have been forced to close all internal systems whilst a full analysis of the breach is conducted, with the confidence and trust severely damaged from any client perspective.
The success of this attack highlights the increasing importance of awareness around Social Engineering. Through a myriad of techniques, a complete stranger was able to coerce an Uber employee with system admin access to accept the “push request” on his cell requesting access. Evidently, we was told (quite unbelievably) that the requests would stop if he accepted the request. Once he accepted, this effectively gave the remote attacker complete control. I fully expect the ripple effect of this attack to be felt for some considerable time with stolen financial records no doubt finding their way into the hands of those willing to use them for their own personal gain.
Everyone should be aware of the risks that impersonation attempts pose, and it is for this reason that you should always question any access request outside of the expected audience. If it doesn’t look or feel right, or the language used doesn’t match that particular person being impersonated, do not provide the access.
@phenomlab Very good article that I would put on my forum if you don’t mind.
-
@phenomlab Very good article that I would put on my forum if you don’t mind.
@DownPW Of course. No issues at all.
Thanks
-
In the news are several reports that Uber has once again become the victim of a large scale (this time with extremely wide ranging implications) attack on it’s internal network infrastructure. One security vendor has already described the breach as by far more extensive than the 2016 global incident (which impacted all of Uber’s entities).

The hacker, who claimed to be 18 years old, told NYT he had sent a text message to an Uber employee and was able to persuade the staff member to reveal a password after claiming to be a corporate information technology employee. The relatively simple social engineering hack allowed him to breach Uber’s systems, with the hacker describing the company’s security posture as weak. The huge gain from the perspective of any bad actor is that the level of access obtained is typically referred to as “god mode” (gamers might be familiar with this phrase, making your character invincible via a number of cheats). Essentially, this is much like an “access all areas” pass with absolutely no locked doors, or any area off limits in terms of Uber’s internal network infrastructure.
The real problem with “god mode” is that it allows the holder to assume complete control over systems without addition challenge, and essentially, lock out the original owner (Denial of Service) – basically, a complete compromise. If you’ve seen Die Hard 2, then you may remember that the plot involved an attack on Dulles Tower where all of the runways, flight management systems, and radar etc. were in full control of a remote entity who’d setup communication links in the adjacent church with the real tower being completely powerless whilst sea level was re-calibrated to minus 200ft causing a landing plane to hit the runway far earlier than they anticipated. Clearly, this is all very “Hollywood” – although it’s 100% feasible as the Uber breach has easily demonstrated and proved.
The impact on Uber is unimaginable – to the extent where they have been forced to close all internal systems whilst a full analysis of the breach is conducted, with the confidence and trust severely damaged from any client perspective.
The success of this attack highlights the increasing importance of awareness around Social Engineering. Through a myriad of techniques, a complete stranger was able to coerce an Uber employee with system admin access to accept the “push request” on his cell requesting access. Evidently, we was told (quite unbelievably) that the requests would stop if he accepted the request. Once he accepted, this effectively gave the remote attacker complete control. I fully expect the ripple effect of this attack to be felt for some considerable time with stolen financial records no doubt finding their way into the hands of those willing to use them for their own personal gain.
Everyone should be aware of the risks that impersonation attempts pose, and it is for this reason that you should always question any access request outside of the expected audience. If it doesn’t look or feel right, or the language used doesn’t match that particular person being impersonated, do not provide the access.
@phenomlab said in Uber breached:
In the news are several reports that Uber has once again become the victim of a large scale (this time with extremely wide ranging implications) attack on it’s internal network infrastructure. One security vendor has already described the breach as by far more extensive than the 2016 global incident (which impacted all of Uber’s entities).
The hacker, who claimed to be 18 years old, told NYT he had sent a text message to an Uber employee and was able to persuade the staff member to reveal a password after claiming to be a corporate information technology employee. The relatively simple social engineering hack allowed him to breach Uber’s systems, with the hacker describing the company’s security posture as weak. The huge gain from the perspective of any bad actor is that the level of access obtained is typically referred to as “god mode” (gamers might be familiar with this phrase, making your character invincible via a number of cheats). Essentially, this is much like an “access all areas” pass with absolutely no locked doors, or any area off limits in terms of Uber’s internal network infrastructure.
The real problem with “god mode” is that it allows the holder to assume complete control over systems without addition challenge, and essentially, lock out the original owner (Denial of Service) – basically, a complete compromise. If you’ve seen Die Hard 2, then you may remember that the plot involved an attack on Dulles Tower where all of the runways, flight management systems, and radar etc. were in full control of a remote entity who’d setup communication links in the adjacent church with the real tower being completely powerless whilst sea level was re-calibrated to minus 200ft causing a landing plane to hit the runway far earlier than they anticipated. Clearly, this is all very “Hollywood” – although it’s 100% feasible as the Uber breach has easily demonstrated and proved.
The impact on Uber is unimaginable – to the extent where they have been forced to close all internal systems whilst a full analysis of the breach is conducted, with the confidence and trust severely damaged from any client perspective.
The success of this attack highlights the increasing importance of awareness around Social Engineering. Through a myriad of techniques, a complete stranger was able to coerce an Uber employee with system admin access to accept the “push request” on his cell requesting access. Evidently, we was told (quite unbelievably) that the requests would stop if he accepted the request. Once he accepted, this effectively gave the remote attacker complete control. I fully expect the ripple effect of this attack to be felt for some considerable time with stolen financial records no doubt finding their way into the hands of those willing to use them for their own personal gain.
Everyone should be aware of the risks that impersonation attempts pose, and it is for this reason that you should always question any access request outside of the expected audience. If it doesn’t look or feel right, or the language used doesn’t match that particular person being impersonated, do not provide the access.
Wow

-
@phenomlab said in Uber breached:
In the news are several reports that Uber has once again become the victim of a large scale (this time with extremely wide ranging implications) attack on it’s internal network infrastructure. One security vendor has already described the breach as by far more extensive than the 2016 global incident (which impacted all of Uber’s entities).

The hacker, who claimed to be 18 years old, told NYT he had sent a text message to an Uber employee and was able to persuade the staff member to reveal a password after claiming to be a corporate information technology employee. The relatively simple social engineering hack allowed him to breach Uber’s systems, with the hacker describing the company’s security posture as weak. The huge gain from the perspective of any bad actor is that the level of access obtained is typically referred to as “god mode” (gamers might be familiar with this phrase, making your character invincible via a number of cheats). Essentially, this is much like an “access all areas” pass with absolutely no locked doors, or any area off limits in terms of Uber’s internal network infrastructure.
The real problem with “god mode” is that it allows the holder to assume complete control over systems without addition challenge, and essentially, lock out the original owner (Denial of Service) – basically, a complete compromise. If you’ve seen Die Hard 2, then you may remember that the plot involved an attack on Dulles Tower where all of the runways, flight management systems, and radar etc. were in full control of a remote entity who’d setup communication links in the adjacent church with the real tower being completely powerless whilst sea level was re-calibrated to minus 200ft causing a landing plane to hit the runway far earlier than they anticipated. Clearly, this is all very “Hollywood” – although it’s 100% feasible as the Uber breach has easily demonstrated and proved.
The impact on Uber is unimaginable – to the extent where they have been forced to close all internal systems whilst a full analysis of the breach is conducted, with the confidence and trust severely damaged from any client perspective.
The success of this attack highlights the increasing importance of awareness around Social Engineering. Through a myriad of techniques, a complete stranger was able to coerce an Uber employee with system admin access to accept the “push request” on his cell requesting access. Evidently, we was told (quite unbelievably) that the requests would stop if he accepted the request. Once he accepted, this effectively gave the remote attacker complete control. I fully expect the ripple effect of this attack to be felt for some considerable time with stolen financial records no doubt finding their way into the hands of those willing to use them for their own personal gain.
Everyone should be aware of the risks that impersonation attempts pose, and it is for this reason that you should always question any access request outside of the expected audience. If it doesn’t look or feel right, or the language used doesn’t match that particular person being impersonated, do not provide the access.
Wow

@JAC Yes, not clever at all, and not the first time either (or even the last in my view)
-
 undefined phenomlab moved this topic from Security on 6 Oct 2022, 14:25
undefined phenomlab moved this topic from Security on 6 Oct 2022, 14:25
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (ether email, or push notification). You'll also be able to save bookmarks, use reactions, and upvote to show your appreciation to other community members.
With your input, this post could be even better 💗
RegisterLog in