Dodgy PayPal emails and how to spot them
-
The dodgy email has been around for some time - often varying in complexity. In most cases, the attempts at spoofing one of the emails is generally very poor. Ranging from incorrect fonts, colour schemes, and overall layout, most of these are really easy to spot. However, the game seems to have been “upped” somewhat over the past few months, and yesterday evening, I received this very convincing email - supposedly from PayPal in my inbox
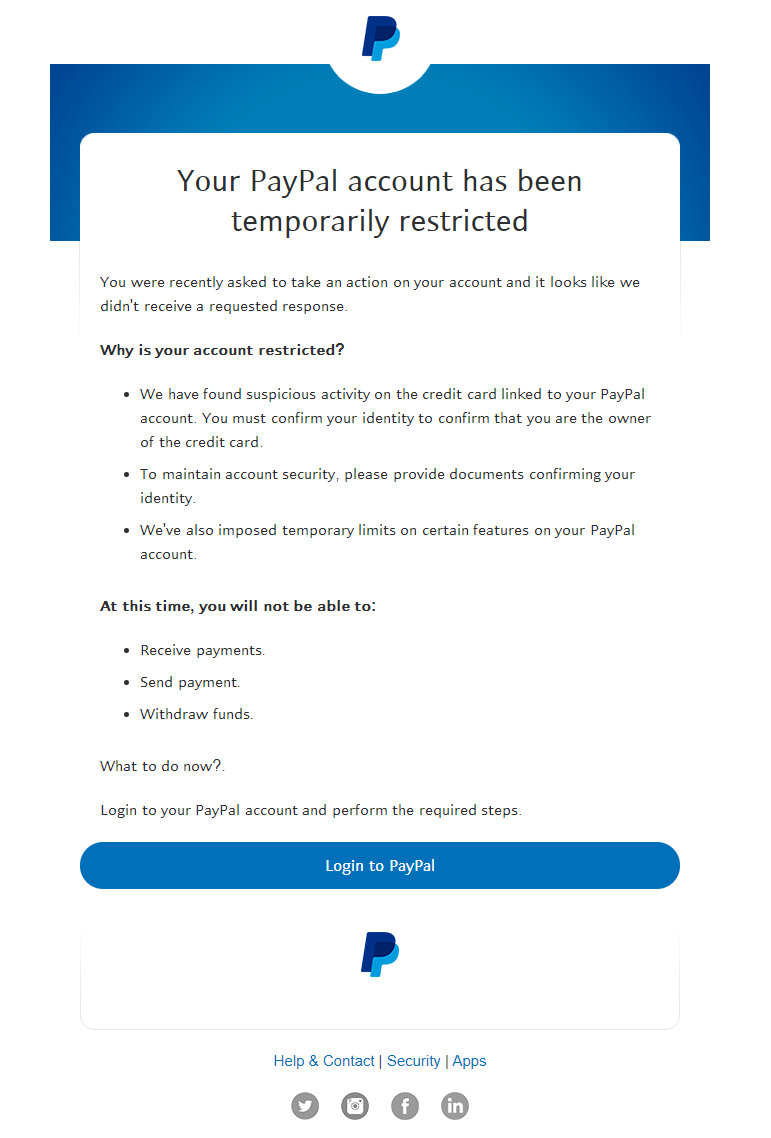
Now, to the untrained eye, this could look very convincing indeed. Should we do as they ask ? Hold it right there. Let’s break down this email by first looking at the address to see who actually sent it
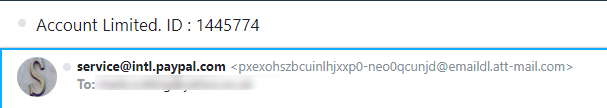
Yeah, that’s not PayPal is it ? It’s some random address a somewhat nefarious individual has created in order to make it look like it’s from PayPal themselves. In most cases, you can easily mask the fake address by placing the “real” one as the “sent from” - in this instance, it looks as though PayPal sent it, but if you dig deeper, this isn’t the case.Another way we can see where the message originated from is to check the message headers themselves.
The first 5-10 lines of the message header gives us insight into the origins of the message. Here’s those very lines from the message I received
Received: from 10.200.76.142 by atlas220.free.mail.ir2.yahoo.com with HTTPS; Thu, 9 Dec 2021 22:22:26 +0000 Return-Path: <9C1pbZ6mPTYKkb0ENR1h4vEzyvGs2GiPxdcooHot@paktron.info> X-Originating-Ip: [209.85.128.103] Received-SPF: pass (domain of paktron.info designates 209.85.128.103 as permitted sender) Authentication-Results: atlas220.free.mail.ir2.yahoo.com; dkim=unknown; spf=pass smtp.mailfrom=paktron.info;As you can see from the last line, the domain that **ACTUALLY **sent the message was “paktron.info”, and definitely not PayPal.
Digging even further, we can also see that “paktron.info” uses Gmail to relay it’s emails
X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=1e100.net; s=20210112; h=x-gm-message-state:date:to:from:subject:message-id:mime-version :content-transfer-encoding; bh=JDzBYqxLWbyz1euLpGy5I34M1DgaEIWD1DyTSYgKsOU=; b=TfLkxbgWVIYonMrIzqbetxzD+F1D3Tf4wHm+l4svGqQH96cM0Og7XVAQtnfe2taJ8c g4T71omH7gq2AGk3zzz09RjjyE47taZhx1p5VhZWkQ93LuAnRZvszLg+QkW59SIHqBs0 bgUzEKtJN3V4pm8YX4XR8KE6+OBRs4ma6GbnOg2n0xW5RPN6WBDihA3PyYB9Ve4GOS+H DCaOlLdJcBq7ftf3ska5Jp4vOAcM/ZTJ0hgjv8ZUf7N08a7gUTcKRnykRkwn0hYUnjlh lImEHPd8S1e4lGLFPpJVMkp1EvRgRBjcPbPIOlcSCgpeBlq2MOFdywcjbHWG2ptC5g5W rP7A== X-Gm-Message-State: AOAM531L2V7LNH6Y/goIZUfnCa5gvlMbyHFvBdrK/9PBccraWnlFrqkr zwyg/3GLjdJrLPJTVWHmgzlc2QEzzZ9tlHG4hRyBao96vaifQ9enb75yoAEM5jzUDA== X-Google-Smtp-Source: ABdhPJwpppASrcH9t3k4kQJ12BODF4ra+WqBwbTQJMjq3PIk+TIemDoplAtzOjynJsvKoSe0ECKHYHQQNxu1 X-Received: by 2002:a1c:ed0a:: with SMTP id l10mr10968558wmh.140.1639088545974; Thu, 09 Dec 2021 14:22:25 -0800 (PST) Received: from notifications-317.loccitane.com ([2a04:ecc0:8:a8:4567:234f:0:1]) by smtp-relay.gmail.com with ESMTPS id m15sm75873wmg.19.2021.12.09.14.22.25 And to confirm this, a quick “whois” will show us that the domain registrar is in fact, Google.
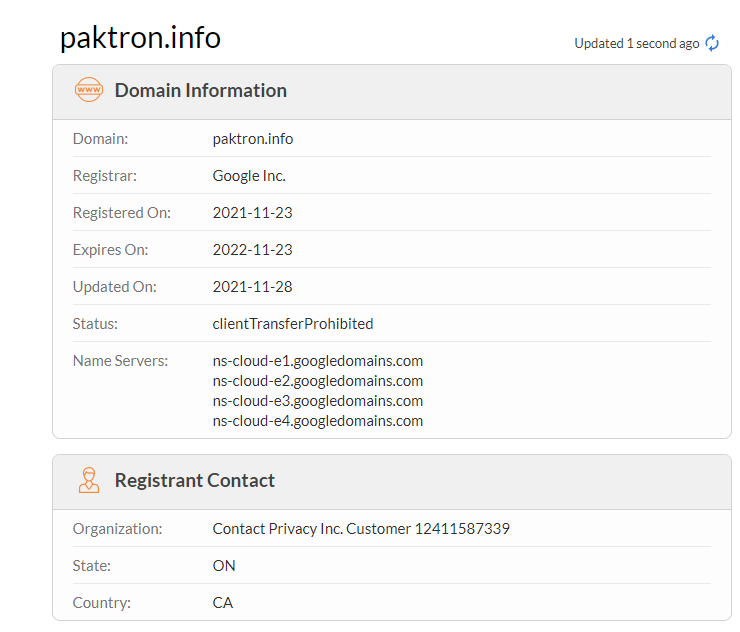
Admittedly, it has privacy protection, so it’s not “Google” per se, but the domain was registered in November 2021, and is relatively new so it pretty clear it’s purpose is solely to send malicious email given that there is no web presence for it.If we also look at the underlying source code of the message we received, we can also see that the “Login to PayPal” button isn’t all what it seems - in fact, it wants to send us somewhere completely different - no doubt a malicious site that looks like PayPal, but in fact isn’t.
target="_blank" href="https://l.wl.co/l?u=https%3A%2F%2Fme2.do%2FG0YhbPsc&signature=JmhXt100uR&trackingid=JijD70jaqr27E&=1" style="text-decoration:none;color:#ffffff !important;white-space:nowrap;">𝖫𝗈𝗀𝗂𝗇 𝗍𝗈 𝖯𝖺𝗒𝖯𝖺𝗅 </a></td>It’s becoming increasingly common for attackers to “hide” malicious links inside “URL Shorteners” as a attempt to mask the real link. Clicking on this link within a sandbox environment takes us here
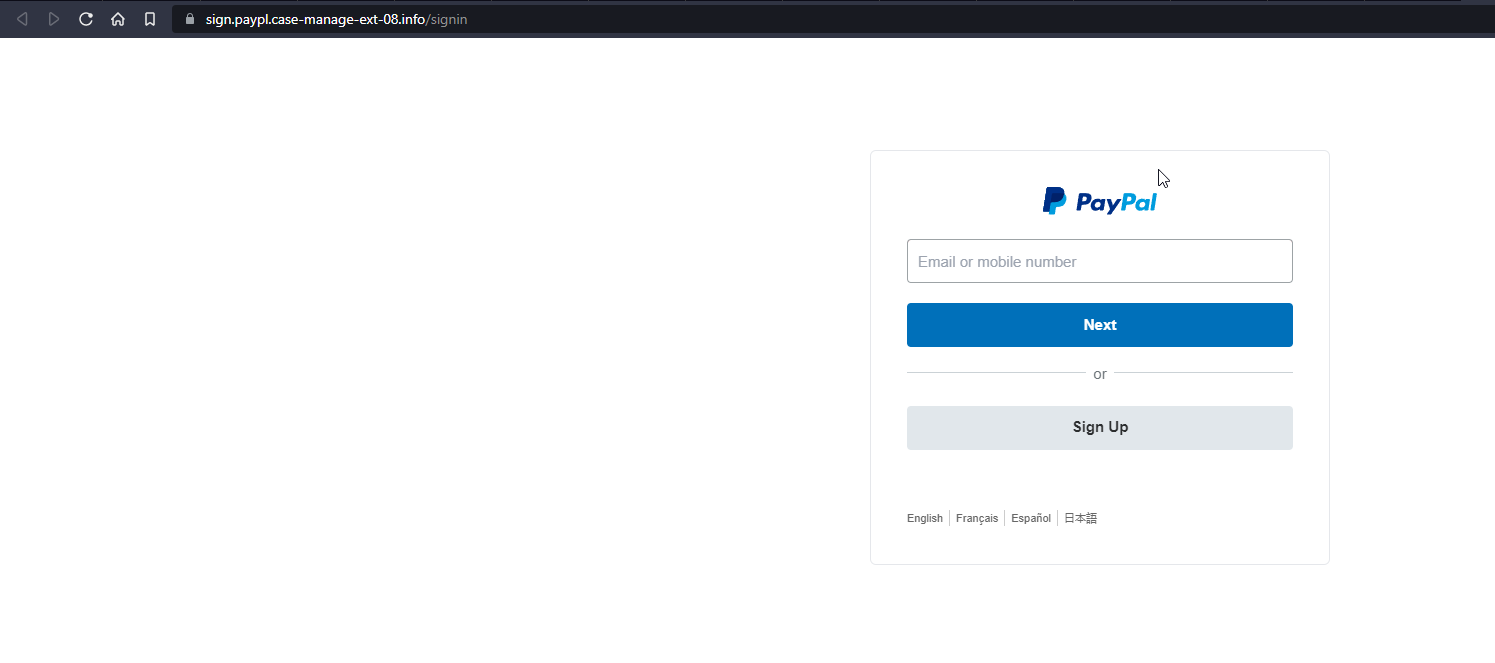
And if we check the URL itself against the vast variety of malicious link checkers, we can easily see that it’s not all it purports to be
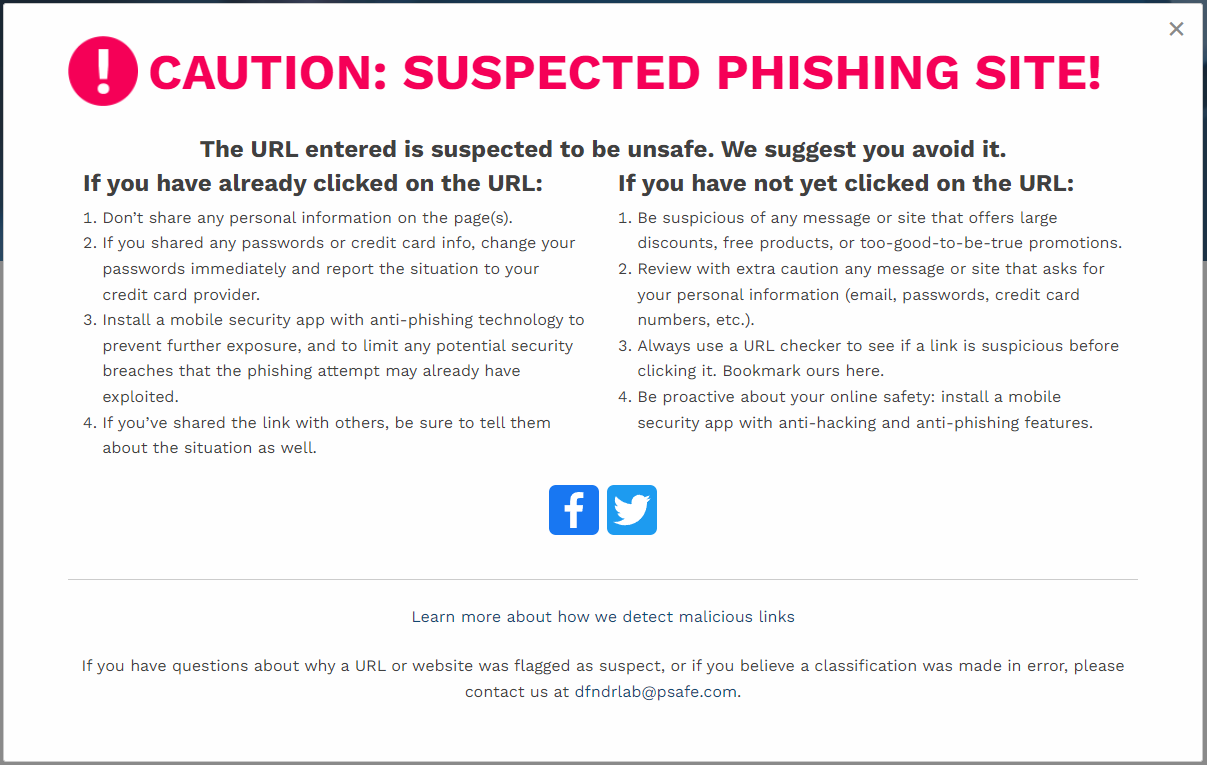
And there you have it. It’s a known “Phishing” site - so called, because it is literally “fishing” for information that you could well readily provide thinking it was your PayPal account you were logging into. Chances are that nothing would actually happen once you submitted your details, but all you’ve dine here in fact is to provide the login ID and password of your PayPal account to an attacker.One of the best ways of avoiding this scenario in the first place is of course to question the email being sent. For example
- Does the email address who sent it match any of PayPal’s ?
- Are there grammatical errors such as poor spelling, or generally bad punctuation ?
- If you hover your mouse over any buttons or links, most email clients will show you the link that is hiding underneath it. Does it look like PayPal ?
- Is the address you’ve received the email on actually registered anywhere with PayPal ?
Protection of your PayPal account is key. One of the strongest methods of protection is to enforce two factor authentication. This essentially extends the login requirement to a username, password, and something only you have - in this case, the 6 digit code (or push notification if you use the PayPal app itself) which is only available on a device in your possession. Even if an attacker did manage to get your username and password, they still wouldn’t be able to login without the code being provided.
Having said that, it’s not difficult to hijack a SIM card so that any attacker wanting to obtain the two factor code via SMS could actually be in a position to do so.
That’s a topic of discussion for another post though…

Stay safe out there - let me know if any questions.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (ether email, or push notification). You'll also be able to save bookmarks, use reactions, and upvote to show your appreciation to other community members.
With your input, this post could be even better 💗
RegisterLog in


