how to use CF tunnels with Virtualmin?
-
how to use CF tunnels with Virtualmin? suggest me a video or doc. is it good to use tunnels. for beginners like me, i think it is the easy way to keep the bad guys away.
is this doc useful? i prefer GUI instead of commands
-
@phenomlab i use a dynamic IP and afraid of DDOS attacks
@Hari understood, but you should consider the basics which always work well if they are configured properly before taking the plunge into what cloudflare offer in terms of tunnels. It’s also perfectly feasible to create an SSH tunnel to access VirtualMin from the web GUI.
A much better method of security would be to place VirtualMin (the admin GUI interface) in an internal virtual adapter that is only accessible when using a VPN. This means that without accessing the VPN first, you cannot use the VirtualMin GUI.
It’s explained here in terms of setting up OpenVPN on VirtualMin/Webmin
Also, don’t be under any illusion that this will prevent a DDoS attack against your site. In most cases, the site itself is leveraged in the attach to overwhelm the server hosting it. There are numerous techniques you can deploy - I’ve of them being Fail2Ban which is actually installed with VirtualMin and ready to configure - and it’s working out of the box once VirtualMin is installed.
Clearly you don’t want to be putting your actual website behind a VPN. That would be little and would make your site fall into the deep web classification in the sense that it would never be crawled, meaning no SEO which I know is important for you.
It would be worth checking what your hosting provider has in terms of DDoS mitigation and if that extends to your VPS. In most cases, the host can prevent a raft of attacks from even hitting your server directly.
-
how to use CF tunnels with Virtualmin? suggest me a video or doc. is it good to use tunnels. for beginners like me, i think it is the easy way to keep the bad guys away.
is this doc useful? i prefer GUI instead of commands
https://serverfault.com/questions/1025551/connecting-to-webmin-gui-remotely-via-ssh-tunnel
@Hari why do you want to do this ? It’s unnecessarily complex when you can secure VirtualMin itself to only listen from approved IP addresses, and also use 2fa.
-
@Hari why do you want to do this ? It’s unnecessarily complex when you can secure VirtualMin itself to only listen from approved IP addresses, and also use 2fa.
@phenomlab i use a dynamic IP and afraid of DDOS attacks
-
@phenomlab i use a dynamic IP and afraid of DDOS attacks
@Hari understood, but you should consider the basics which always work well if they are configured properly before taking the plunge into what cloudflare offer in terms of tunnels. It’s also perfectly feasible to create an SSH tunnel to access VirtualMin from the web GUI.
A much better method of security would be to place VirtualMin (the admin GUI interface) in an internal virtual adapter that is only accessible when using a VPN. This means that without accessing the VPN first, you cannot use the VirtualMin GUI.
It’s explained here in terms of setting up OpenVPN on VirtualMin/Webmin
Also, don’t be under any illusion that this will prevent a DDoS attack against your site. In most cases, the site itself is leveraged in the attach to overwhelm the server hosting it. There are numerous techniques you can deploy - I’ve of them being Fail2Ban which is actually installed with VirtualMin and ready to configure - and it’s working out of the box once VirtualMin is installed.
Clearly you don’t want to be putting your actual website behind a VPN. That would be little and would make your site fall into the deep web classification in the sense that it would never be crawled, meaning no SEO which I know is important for you.
It would be worth checking what your hosting provider has in terms of DDoS mitigation and if that extends to your VPS. In most cases, the host can prevent a raft of attacks from even hitting your server directly.
-
undefined phenomlab has marked this topic as solved on 19 May 2022, 13:34
-
@Hari That’s not the first time either
-
ELI5 (explain me like five year old)
What are tunnels? Why we should or shouldn’t use?
And why youtube or Google never experiences DDoS attacks?
We will be going to Gatsby with graphql + noode js in a month so static sites will not face such issues?
@Hari A tunnel is a point-to-point connection from your workstation directly to your server. This tunnel is encrypted by default, meaning that any transactions or information exchanges taking place between your workstation and server cannot be seen or intercepted by anyone else.
However, in the sense of CF, they will act as the intermediary. So, you connect to CF, and then they provide a bridge for you top reach your destination server securely. There’s nothing wrong with using tunnels, although this isn’t security in the sense that you think it is. For example, for true secured management of servers, you’d need for the server itself to be reachable only by the management NIC, and that would typically via a secured VPN using mandatory 2FA as well as standard username and passwords.
The website itself however, would remain unprotected in this sense though as it needs to be publicly accessible in order to function. It’s perfectly feasible to gain shell access via a website vulnerability, so the VPN in this sense becomes useless as it is easily bypassed by what is effectively classed as back door access to the server via an exposed shell.
YouTube and Google are attacked literally every second. See below for a more detailed explanation of how Cloud Armour is used
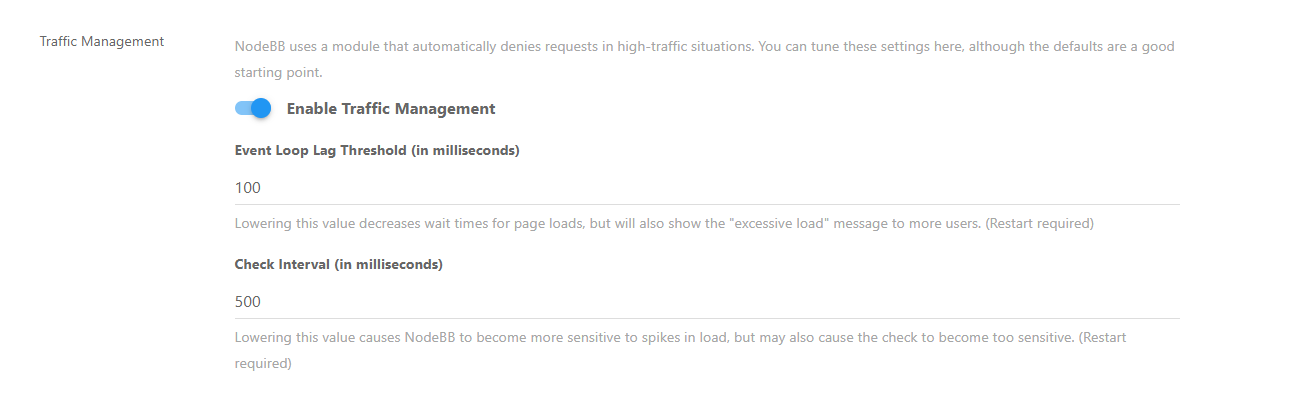
Static sites are never exempt from DDoS attack. Remember that the entire point of a DDoS is to render the remote machine inoperable by sending hundreds of thousands (sometimes millions) of requests per second - not to “hack” it, but to force it offline due to severe load. NodeBB actually has mitigating controls around this
In essence, it’s own “light DDoS” mitigation - in fact, the only platform I’ve seen that has this built in as part of it’s core.
-
Now i understood everything, thanks a lot for detailed explanation.
In case of flarum how i can I protect my own? Does cloudways handles this kind of attacks for me?
If i move out from cloudways to digital ocean plesk or virtualmin will I be able to handle it?
@Hari DDoS protection is not just a switch, or one component. It’s a collection of different and often disparate technologies that when grouped together form the basis of a combined toolset that can be used in defence.
Typically these consist of IDS (Instrusion Detection System) and IPS (Intrusion Prevention System) components that detect irregularities in network traffic, and will take decisive action based on predefined rulesets, or in the case of more modern systems, AI and ML.
Traditional “traffic shaping” technology is also deployed, so if an attack cannot be easily identified as malicious, the bandwidth available to that connection is severely limited to nothing more than a trickle rather than a full flow.
Years ago, ISP’s used traffic shaping (also called “policers”) as an effective means of stopping applications such as BearShare, eDonkey, Napster, and other P2P based sharing systems from functioning correctly - essentially reducing the “appeal” of distributing and seeding illegal downloads. This was essentially the ISP’s way of saying “stop what you are doing please” without actually pulling the plug.
These days, DDoS attacks are designed to overwhelm - not assume control of - webservers and other public facing components. It’s rare for small entities to be attacked unless there is some form of political agenda driven by your site or product. A classic example is governmental institutions or lawmakers who effectively are classed as “enforcers” and those who disagree are effectively making a statement in the form of Denial of Service.
DDoS protection is effectively the responsibility of the hosting provider, but you shouldn’t just assume that they will protect you or your site. Their responsibility stops at their infrastructure, so it’s then up to you too decide how you full the gap in between your host and the website.
Typically, you’d leverage something like Imunify360 which you can get for Plesk (and something I’d strongly recommend) but it’s not free, and is a paid (not expensive per month) subscription. If you want to use VirtualMin then there are a variety of tools readily available out of the box such as firewalls and fail2ban.
Did this solution help you?
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (ether email, or push notification). You'll also be able to save bookmarks, use reactions, and upvote to show your appreciation to other community members.
With your input, this post could be even better 💗
RegisterLog in